Automotive Cyber & Privacy Liability – Risks & Mitigation

The Connected and Autonomous Vehicles (CAVs) revolution is ushering in significant benefits in convenience, safety, information, communication, and entertainment options for consumers. It also has the potential to eliminate virtually all accidents; drastically reduce traffic congestion; and providing an economical and environmentally friendly mode of transportation. But to deliver these benefits, a variety of technologies are becoming embedded into CAVs and they work on over 100 million of lines of code – manifold times more than aircrafts – with over 30,000 component parts and 30-100 electronic control units (ECUs).1 These numbers are set to explode in the coming decades.2

The explosion in software and data intensity in CAVs, make them a potential target for hacking and therefore CAVs need to be continuously secured, patched, and updated. It is estimated that there are at least 15 key issues that can be hacked in most connected cars.4
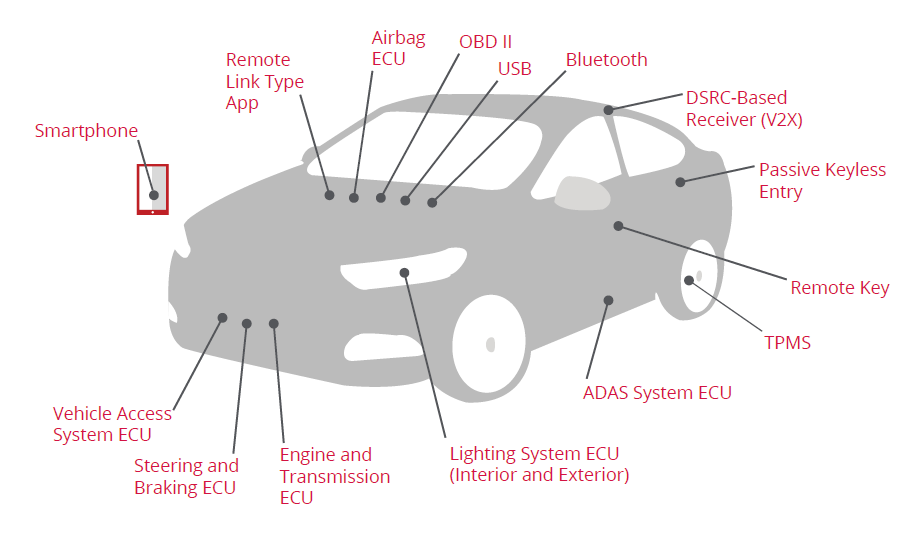
The fast-paced changes in automotive, electronic technologies, have shortened automotive development and production cycles.5 But, while the adoption rate of new technologies has increased exponentially, cybersecurity measures are not able to keep pace with these rapid developments and are causing a sharp increase in the cyber risk.6 Further, the number of attack vectors in connected cars and the automotive industry is significant leaving many cybersecurity gaps open and unresolved, endangering customer safety along with higher risk of financial and reputational harm for businesses.7
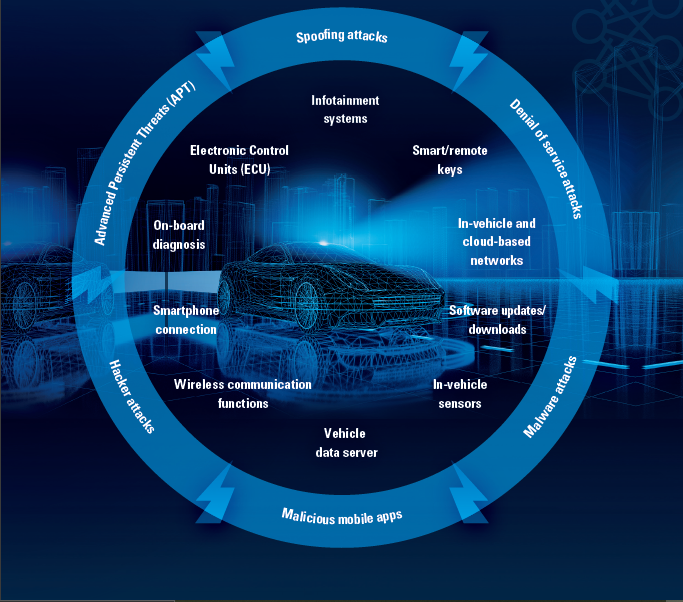
The consequences of cyberattacks on connected automobiles, will be devastating for all stakeholders – car owners, OEMs, service providers, the public, government, and society.8
| Driving functions failLoss of brake controlLoss of engine controlLoss of steering control | Vehicle systems failDysfunctional door locksInoperative lightsDisrupted passenger safety systems Faulty diagnostics | CollisonLiability questionsDriver injuries or deathsPedestrian injuries or deaths |
| Data theftInfrastructure dataPersonal dataVehicle data | Vehicle theftTrack vehicle’s GPS coordinates Manipulated navigationTelematicsTakeover controlVehicle sold/held to ransom | Commercial lossBrand damageReduced buyer confidenceRevenue loss |
To meet the need for enforcement of automotive cybersecurity, the European Union (EU), Japan and other major markets have adopted UN-ECE-WP.29, a set of cybersecurity regulations that defines principles to address key cyber threats and vulnerabilities identified in order to assure vehicle safety in case of cyber-attacks. UN-ECE-WP.29 is being implemented through ISO/SAE 21434, “Road vehicles — Cybersecurity engineering”, a set of guidelines for ensuring automotive cybersecurity. Under this, Automotive OEMs and suppliers are required to continually detect and react to security issues during the entire lifespan of the vehicle. CAVs will be under live monitoring and analysis from Vehicle Security Operation Centers (V-SOCs), where vehicle data is continuously transmitted back to a V-SOC for analysis and monitoring whether an attack is taking place, and for remedial action to be taken swiftly.
V-SOCs – Data Privacy Issues
V-SOC will have access to data on cybersecurity systems, as well as vehicular data that is needed for enabling repairs, to ensure and promote security both in vehicles and on the road, identify and predict performance and maintenance. However, privacy laws like the California Consumer Privacy Act (CCPA) define personal information as the “information that identifies, relates to, describes, is capable of being associated with, or could reasonably be linked, directly or indirectly, with a consumer or household.” Majority of the data that is collected by a vehicle, fall under this definition:
- Information about a vehicle’s functionality, such as mileage, fuel consumption, oil levels, engine status, temperature or speed;
- information about the vehicle’s performance, operation and environment, such as where it is located and how it responds in certain weather conditions or at certain speeds;
- maintenance information, including when the vehicle has been serviced and when the next service may be required
- any malfunction reports.
- On-board diagnostics systems or the telematics systems — in other words, information that is collected via the communication or infotainment systems and/or via driver inputs, such as the location of the driver’s home or office.
- Biometric information, or whether the driver is drunk or is too tired to operate the vehicle
While, this data can be used by manufacturers and service providers to ensure vehicle operation and efficient repairs and services, but it involves the privacy of the vehicle owners or driver. To comply with CCPA, “Car manufacturers and service providers should conduct an inventory of what data they collect and use…., where the data is sent and for what purpose. …To the extent that the data collected by a car is classified as personal information, there are a number of rights that must be granted…., including: Notice, Access, Opt-out or -in, Deletion, Equal services and prices regardless of choices made.”9 Under the CCPA, consumers have broad rights to personal information collected about them, including information collected by vehicle manufacturers, dealers and service providers. The consumer the right to know what data is held about them, and the CCPA requires carmakers to ensure that there are systems in place to ensure the consumer is given that right.
Product Liability and Cyber / Privacy Liability
Automotive Cybersecurity in CAVs gives rise to several issues relating to product liability10 and cyber / privacy breach liability
- In case of incidents with a certified product, there are important questions relating to
- the liability of manufacturers, distributors, conformity assessment bodies, and consumers.
- Liabilities regarding the convergence between product safety and security
- are consumers responsible for the damage of an incident if they did not update their IoT device regularly?
- At what point can a manufacturer of an IoT device stop providing important security updates? Given the crucial role of secure and regularly updated software for a device’s functioning?
- Liability relating to responsibilities for informing users of IoT devices about known vulnerabilities and disclosing security breaches.
Mitigation of Cyber and Privacy Risks in IoT
Cybersecurity and privacy risks for IoT devices, can be addressed through three high-level risk mitigation goals, as recommended by NIST 11.
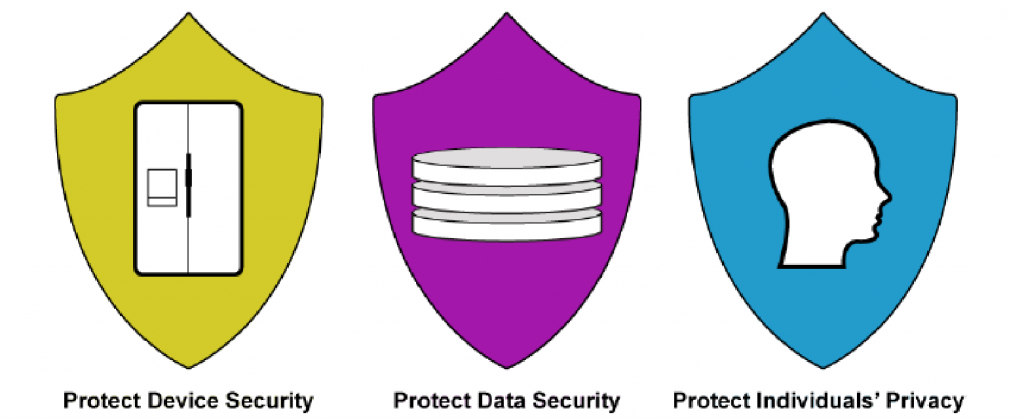
- Protect device security. Prevent a device from being used to conduct attacks, including participating in distributed denial of service (DDoS) attacks against other organizations, and eavesdropping on network traffic or compromising other devices on the same network segment.
- Asset Management: Maintain a current, accurate inventory of all IoT devices and their relevant characteristics throughout the devices’ lifecycles in order to use that information for cybersecurity and privacy risk management purposes.
- Vulnerability Management: Identify and eliminate known vulnerabilities in IoT device software and firmware in order to reduce the likelihood and ease of exploitation and compromise.
- Access Management: Prevent unauthorized and improper physical and logical access to, usage of, and administration of IoT devices by people, processes, and other computing devices.
- Device Security Incident Detection: Monitor and analyze IoT device activity for signs of incidents involving device security.
- Protect data security. Protect the confidentiality, integrity, and/or availability of data (including PII) collected by, stored on, processed by, or transmitted to or from the IoT device.
- Data Protection: Prevent access to and tampering with data at rest or in transit that might expose sensitive information or allow manipulation or disruption of IoT device operations.
- Data Security Incident Detection: Monitor and analyze IoT device activity for signs of incidents involving data security.
- Protect individuals’ privacy. Protect individuals’ privacy impacted by PII processing beyond risks managed through device and data security protection.
- Information Flow Management: Maintain a current, accurate mapping of the information lifecycle of PII, including the type of data action, the elements of PII being processed by the data action, the party doing the processing, and any additional relevant contextual factors about the processing to use for privacy risk management purposes.
- PII Processing Permissions Management: Maintain permissions for PII processing to prevent unpermitted PII processing.
- Informed Decision Making: Enable individuals to understand the effects of PII processing and interactions with the device, participate in decision-making about the PII processing or interactions, and resolve problems.
- Disassociated Data Management: Identify authorized PII processing and determine how PII may be minimized or disassociated from individuals and IoT devices.
- Privacy Breach Detection: Monitor and analyze IoT device activity for signs of breaches involving individuals’ privacy.
Further, mitigation of Cyber Security and Data Protection risks can be obtained from Cyber Insurance policies that offer cover for cyber or privacy breaches.12
Third Party V-SOCs – Potential Solution
The likely enactment of the Personal Data Protection law in India, will extend the CCPA type privacy regime. To meet the requirements of privacy law, the solution could be through a tweaking the V-SOCs from Manufacture Operated to Independent 3rd Party V-SOCs that can be modelled on the National Securities Depository (NSDL) and Central Securities Depository (CDSL), in stock markets. This model will ensure that all the privacy related principles of CCPA, PDP, GDPR will be implemented effectively and simultaneously, critical vehicle and driver data can be shared (with the explicit consent of the data principal) with insurance companies and law enforcement authorities, for monitoring and measurement of vehicle and driver risk profiles. Risk-adjusted fixation of vehicle insurance and accident insurance premiums will go a long way in incentivizing positive driver behavior and practices, while penalizing adverse patterns.
Road Safety
The United Nations Sustainable Development Goals (SDG) stipulates the following goals.
- SDG 3.6 By 2020 halve the number of global deaths and injuries from road traffic accidents
- SDG 11.2 By 2030 provide access to safe, affordable, accessible and sustainable transport systems for all, improving road safety, notably by expanding public transport, with special attention to the needs of those in vulnerable situations, women, children, persons with disabilities and older person.
In India, the combination of CAVs and 3rd Party V-SOCs will assist in achieving the SDG goals, by a judicious mix of incentives / disincentives for safe driving behavior, through risk-adjusted motor insurance premium. We can look forward to a minimum of 10% savings in Motor Insurance premiums, which stands at Rs.69208 Crores for FY2019-20, through reduced accidents, injuries, and deaths.13
As Sanjay Gupta, Vice President & India Country Manager – NXP Semiconductors recommends, “it is important that all stakeholders fulfill their roles: government agencies, industry players as well as car owners. Requesting information about the security capabilities of our cars should become routine, in the same way as we learn about safety, driving parameters and convenience features today. Providers must support this goal with the most advanced technology, so we can all be safe and secure while moving towards the future of mobility.”14
References
1 “Who is responsible for securing the connected car?”, NTT Security, 2019
2 TUV SUD (2018), “Potential Cyber Security Threats Of Autonomous And Connected Vehicles: Consequences And Safety Solutions”
3TUV SUD (2018)
4 McCafe, Automotive Security – Best Practices, 2016
5 Chad Morley. (n.d.). Jabil. “Automotive Industry Life Cycle – Shorter Timelines.” https://www.jabil.com/blog/automotive-industry-trends-point-to-shorter-product-development-cycles.html.
6 Johannes Deichmann et al. McKinsey & Company. (2019) “The race for cybersecurity: Protecting the connected car in the era of new regulation.”
7 TUV SUD (2018)
8 TUV SUD (2018)
9 Eva Pulliam & Sarah Bruno, “CCPA’s potential impact in the automotive space”, IAPP, Oct 2019
10 “Securing the Internet of Things Together”, Indo-German Working Group on Quality Infrastructure, GIZ, January 2020
11 NIST, “Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks- NISTIR 8228”, June 2019
12 Automotive IQ, May 2018, “8 Tips to Prevent Autonomous Vehicle Cyber Breach Liability”.
13 “Cyber Governance in Motor Insurance in India”, Working Paper, Japan-India Development Forum, April 2020.
14“Unauthorised vehicle access, loss of personal info: Connected cars need better cybersecurity”, Financial Express, Express Drives Desk, Jul 28, 2020
Automotive Cybersecurity in India will lead to overall improvement in Road Safety, reduced Accidents, Injuries, Deaths and will bring a minimum of 10% reduction in Motor Insurance premiums. However, to meet the Privacy regulations under Personal Data Protection law, it is imperative to establish 3rd party V-SOCs as the fulcrum of the automotive cybersecurity ecosystem.
Author:
Arjun Bhaskaran, is Country Manager – India & Middle East for Gamasec an Israel based Cybersecurity company that is pioneering new models in Cyber & Privacy Liability Insurance for Enterprise and SMB markets in OECD countries. He has been CTO, CISO of several companies in the Insurance sector. He was part of a 5 member team that established Axis Bank project from conception to go-live. He can be reached at arjun@gamasec.com
Published in Telematics Wire


