Securing a Connected Car

ABSTRACT
The influx of digital transformation and advancements in technology have enabled the automakers to develop cars that are cleaner, safer, smarter and more energy-efficient. This revolution is being driven by the convergence of connectivity, electrification and demanding customer needs. Today’s cars employ a series of intelligent technologies such as Blind spot detection, Adaptive headlights, Lane keep assist, Collision warning, Adaptive cruise control, Reversing camera, Hill assist, Crash-imminent braking. Further with everyone wanting to stay connected all the time, car designers are making cars in line with this growing trend. This makes the modern-day automobiles more sophisticated, extremely complicated and highly connected systems. While the Connected autonomous technologies are expected to make the cars more safer, more energy efficient, and more intelligent systems the highly connected nature of these cars make them extremely vulnerable to cyber-attacks. By gaining access to the car, hackers can compromise safety critical functions endangering life of the passengers seated in the car. The objective of this article is to discuss about the potential cybersecurity threats in modern vehicles, their impact and the possible counter measures to safeguard the vehicle against potential attacks
INTRODUCTION
Unlike the classic cars, the modern vehicles are software-intensive, more complex, and highly connected systems. They can have about 70-100 embedded microcontrollers onboard running millions of lines of code within them. These ECU’s control almost every function of the car including safety-critical vehicle applications such as braking, engine control, steering, airbag functions, navigation systems etc. Now as cars became more and more interactive, they get connected to the Internet, with each other (V2V), and with the infrastructure (V2X) they become more vulnerable than ever to attackers and hackers. Thus, a modern car architecture provides a broad internal attack surface with each component having at least implicit access to every other component on the bus. A compromised infotainment system can offer an effective vector for attacking safety critical ECU’s connected to the In-vehicle network. Once a hacker gains access to the in-vehicle network of the car, they could control everything; from controlling the acceleration, to applying or releasing brakes, locking or unlocking the doors. Therefore, security attacks are not just limited to theft or disclosure of information, but also affect safety of the passengers seated inside the car
Recent studies and Experiments conducted by Independent research organizations from EUROPE/US (Stephen Checkoway et. al] have demonstrated that once a hacker gain access to the in-vehicle network of the car, could control everything; from controlling the acceleration, to applying and releasing brakes, locking/unlocking the doors. These experiments demonstrate the importance of security in automotive systems.
Security Attacks Overview
The Security attacks can be broadly classified into Active attacks and Passive attacks. The figure below provides an overview of attacks an automotive system can be subjected to
How A Connected Car Can Be Hacked?
A modern automotive can be hacked either by physical access or by remote access of the In-Vehicle-Network. Direct physical access to the car internal network is possible via OBD port, Debug ports or Digital multimedia ports. Remote access to car is possible via a broad range of attack vectors such as CD/DVD players, Short-range wireless access – Bluetooth, RFID(remote Keyless entry, vehicle immobilizers, Tire Pressure Monitoring System), Dedicated Short-Range Communications and Long-range wireless access – WiFi, Cellular Technologies(LTE, GSM, CDMA)
Connected vehicles use a combination of wireless technologies such as Radar, Lidar, GPS and other advanced sensors for its operation. These cars are expected to have a permanent connection to the Internet and to the cloud for fetching various kinds of information such as road speed limit, current traffic situation, weather conditions, traffic light status etc. They can also communicate with other smart devices, other cars and roadside infrastructures for collecting real-time data to make certain decisions. Attacker can intercept and manipulate the messages or send forged messages to the ECU causing them to mal function. Therefore, it is important to understand the various threats a connected car can be subjected to and necessitate the use of robust security measures using modern day crypto techniques to protect the sensitive data from unauthorized access and manipulation
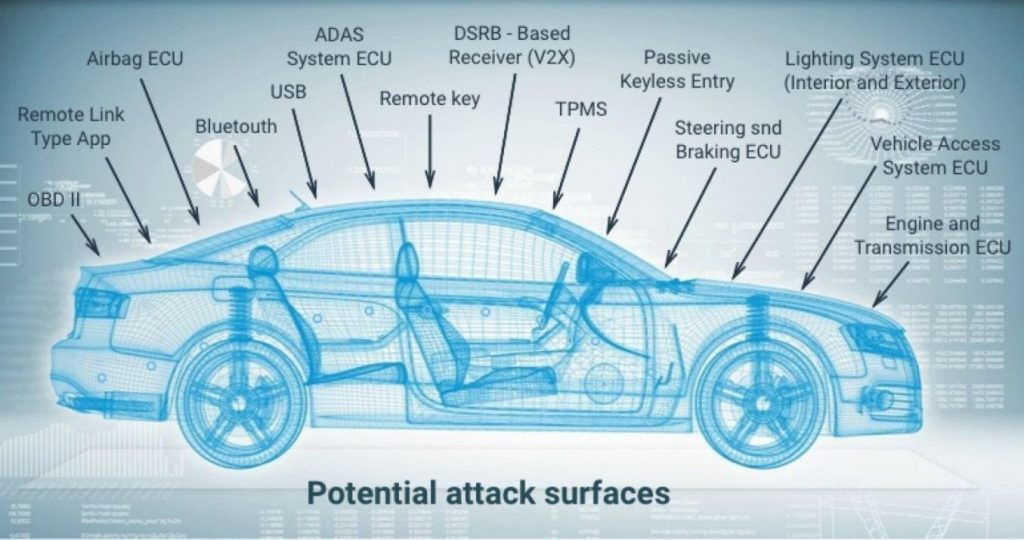
Here are some of the potential attack vectors in a Connected car:
Telematics Control Unit:
Telematics units on a vehicle are the connecting point to the outside world. They support a variety of wireless technologies such as Wi-Fi, Bluetooth, and Cellular Technologies such as LTE, GSM, CDMA. These technologies allow the vehicles to communicate with the Cloud, with the Telematics Service providers, OEM Backends. A hacker can use networking hacking techniques such as port scanning, circumventing firewalls to get unauthorized access to the vehicles via these interfaces. A hacker after compromising the servers at a telematics call center could issue engine disable commands to all cars
Infotainment System:
In-Vehicle Infotainment systems support a wide variety of user Apps. The user Apps provide a variety of services that include access to social media, internet browsing capabilities etc. These internet enabled Infotainment systems serve as a gateway to the car’s internal network enabling hackers to gain control of the critical car functions
Unprotected External Interfaces and Debug Ports
Modern day automobiles can have a number of external interfaces (wired and wireless) and a number of debug ports such as JTAG, XCP which can allow easy access to ECU resources if not protected. Hackers gaining access to these ports can corrupt rewriteable flash memory and inject malicious firmware causing the ECU to malfunction
Wireless Key Entry
Breaking anti-theft systems such as Central locking, Immobilizers, passive keyless entry to gain access to the car
Over the Air Firmware Upgrades
Downloading malicious applications into the ECU could result in erroneous behavior. Malware in an ECU can even download incorrect navigation maps to mislead the driver. This could be one a lucrative business for cyber-criminals. In ransomware attacks, a computer is disabled by the hacker until the victim pays a ransom fee to unlock it. A ransomware infection of a car or commercial truck would be extremely disruptive and costly to both individuals and businesses. Therefore, victims would be more inclined to pay – potentially paying more than they would for a PC or phone.
Insecure communication channels
Lack of mechanisms to check integrity of messages can result in Execution of unauthorized commands, Eavesdropping and sending spoofed messages to the monitoring ECU, Illegal Odometer Tuning
Insider Attacks
An insider threat is a security risk that originates from within the organization. Anyone who has access to the organization’s confidential data is a potential insider threat. It could be an employee, contractor having access to user credentials and sells those secrets to outsiders for making profit.
e-Call Center Attack
A hacker with access to Telematic call center servers could issue engine disable commands to all the cars
Poor Security Policies, Procedures, Practices
Weak Firewall rules, usage of hard coded Keys and passwords, weak keys and passwords, usage of same Keys on all vehicles, lack of access control methods, weak network policy of trusting everyone and every device
Securing a Connected Vehicle
The security system inside autonomous connected vehicle shall ensure that technology in the connected Car works 100% of the time without compromising the safety-critical functions. To achieve this a multi-layered, distributed security architecture with a defense-in-depth strategy is needed. The figure below shows a four Layer Security architecture. Here each layer provides a layer of security contributing to overall defense of the system
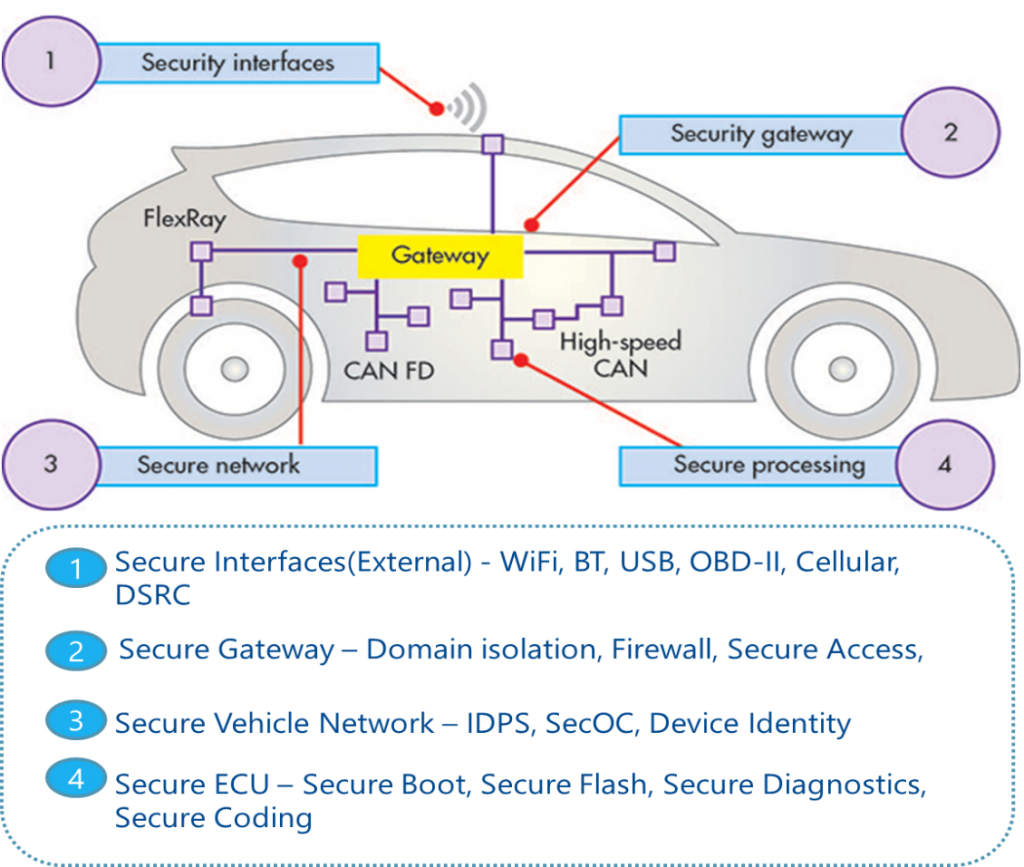
In order to secure the Connected vehicles from cyber-attacks, the automotive system shall implement appropriate security controls based on software and hardware cryptography. The security system must ensure that data is protected during its transit, while it is stored, and while it is accessed. There must be mechanism in place to ensure both unauthorized and unintended modifications do not go undetected. Any remote access shall have multi-factor authentication implemented to reduces the risk of identity theft and unauthorized disclosures. All the above can be achieved through a combination of hardware & software features, physical controls, encryption mechanisms, operating procedures, and various combinations of these.
Here are some Security measures to secure vehicle network:
Off Board Network Security
- V2X Security
- Secure external interfaces
- Remote Diagnostics
- Target Authentication
- Secure Software Updates Over the Air(SOTA)
In-Vehicle Network Security
- Secure Boot
- Secure Flashing
- Secure Access
- Secure Storage
- Secure Onboard Communication(SecOC)
- Secure Diagnostics
- Key Management
- Auditing and Logging
- Hardware based Crypto(HSM/SHE)
- Machine Security & Tamper protection
Automotive Security Standardization
- AUTOSAR, EVITA, HIS, NHTSA, C2CCC
Cybersecurity Best Procedures and Practices:
- Threat Assessment & Risk Management
- Threat Modeling
- Security by Design
- Security Hardening (Secure Coding Practices, MISRA and Cert-C compliance)
- Penetration & Fuzz Testing
- Recovery after Compromise
- Employ security controls at ECU’s and Backend servers to restrict access
Conclusion:
A compromised car not only endangers safety of humans but also involves many other consequences both to the owner and to the Car makers. A successful Cyber-attack can result in financial losses to the OEM due to forensic investigation costs, loss of sensitive data, impact to business, legal costs, compensation to customers, vehicle recall cost. Fortunately, there are many steps that car manufacturers can take to secure the Connected vehicles. These include deploying Network Security mechanisms – separating the safety critical networks from the Internet facing networks, Firewalls, IDPS, Security incident and logging and detection. Implement Security techniques such as Software Signing and Authentication, Secure diagnostics, Secure Communication, Debug port protection.
The modern cryptographic algorithms, when implemented correctly, are highly-resistant to Cyberattacks, however their only weak point is their keys. Therefore, employing robust Key management strategy is very crucial to protect the system from compromise. Last but not the least, follow industry standards & practices such as NIST/FIPS, EVITA, SHE, ENISA, SAE J3061, IEEE 1609.2-2016 while developing Security solutions rather than going with proprietary solutions.
Author:
Software professional with over 18+ years of experience in embedded product development. Main focus area being Automotive Cybersecurity. Have extensive global exposure across multiple industries such as Automotive, HVAC and Security domain.
Published in Telematics Wire

