Automotive Cyber-Security: Separating fear from the fact
Franz Tschimben Sridhar Reddy
Business Development Savari Networks
Savari Inc.
Cyber security has been a big issue for the fast evolving automotive market ever since electronics became a crucial part of the vehicle, but only made it into mainstream media in July 2015. Miller and Valasek exposed the weak points of regular cars on the streets by wirelessly and remotely hacking into a Jeep Cherokee for demonstration purposes. Testing was conducted on a total of 20 car models released from 2014 to 2015 from di?erent manufacturers–the problem is universal and involves the whole industry.
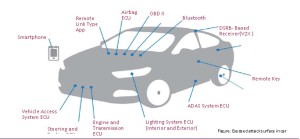
The hacking demonstration of the car happened through the center piece of today’s connected cars: the infotainment system and its cellular connection. As cars will get more connected and autonomous in the years to come, more entry options will be given to software specialists with malicious intentions. Research of the Automotive Security Review Board, led by Intel, shows that 15 exposed attack surfaces exist in the next generation smart car.
One of the biggest and most widely regarded benefits of the connection and automation of cars–reducing total fatal car accidents–is at stake. According to Miller and Valasek, a successful hack depends on remote attack surfaces, cyber physical features and in-vehicle network architectures were the identified.
The industry has given priority to the threat and works towards creating a system that reduces hacking threats by closing down entry points. Importance is given to solutions with software that can be continuously updated and therefore strengthened.
OEM’s, suppliers and specialized automotive cyber security companies like Argus and Towersec, are developing and marketing solutions. Furthermore, the Auto Information Sharing and Analysis Center (ISAC) has been established for major automakers in July 2015. Its chairman, Tom Stricker from Toyota, explained that the group will act as a central hub for gathering intelligence that allows to analyze, share and track cyber threats and spot potential weaknesses in vehicle electronics”.
As the industry is intended to decrease the threat of cyber security by bundling forces, so does legislation by working on a new draft bill–titled “Security and Privacy in your (SPY) car act of 2015” that aims at establishing cyber security standards for car companies and penalties for hackers.
It is crucial to ensure that standards keep getting better over time and evolve just as smart cars are improving and becoming more dependent on electronics hardware and software and hackers are improving their skill-set.
Security risks exist not only in terms of a hacker taking control of the vehicle but also with the aim of negatively impacting the application or service. Savari is working at the forefront of IEEE 1609.x V2X technology, which relies on periodic broadcast of over the air messages between vehicles to vehicles and between vehicles and infrastructure. As a result, V2X provides yet another gateway in and out of the vehicle. We, at Savari believe that it is crucial for Tier I/II automotive suppliers to also take an active role in ensuring that solutions are secure. Threats such as “man in the middle”, vehicle spoofing, etc., could all have a detrimental e?ect on the final user application. It is critical to prevent rogue users from accessing the security certificates. In this regard, on the technology side, incorporating secure technologies like hardware security module (HSM), trusted platform, secure boot and secure updates should be a mandatory minimum. Furthermore, it is vital that security solutions build in features such as reporting, certificate revocation mechanisms, etc.
The V2X solution also incorporates access to the CAN bus. In the future a V2X sensor may not only be used for determining the situational awareness for a vehicle but also for actuation of the vehicle. One way to ensure more security at the CAN level is to create di?erent priority levels to system IO access. This way, even if the system is compromised, the hacker cannot gain control to such vital ports. This approach is likely to require a combination of both Hardware and Software. The OEMs are also looking at making the car more secure by having a secured CAN bus by using authenticated CAN messages, multiple independent CAN buses in order to reduce the attack surface.
Much of the above mechanisms require engineering implementation of these solutions and safety features. Su?cient learnings were gained from the vulnerability of computers, especially from the earlier days of Linux. Crippling Linux servers in the past (and even today) took the form of Denial-of-service (DOS) attacks, source spoofing to email programs that in turn allowed hackers to take control over the systems. Many of these not only require specific implementation of features but also require specific process of development and quality assurance. Across the industry well defined engineering practices are being adopted to follow safety and security standards and best practice guidelines. This includes compliance to MISRAC, automotive SPICE and ISO 26262 The guidelines and certification. This enables security to be considered early on in the lifecycle, software requirement, architecture & design, and testing. Errors or hacking mechanisms that can cause bu?er overflows or similar can now be prevented by incorporation of design and development practices. There are many such tools, components and products available which can be leveraged. Operating system vendors for example, Greenhills and QNX, are providing OS with hypervisor and virtualization support to run safe execution of trusted and critical software side-by-side with untrusted application.

