Automotive Ethernet Networks Are Changing the Security Paradigm
Michal Frenkel, Argus Cyber Security
Ran Ben Tzvi, Argus Cyber Security
One of the more significant developments in vehicle architectures in recent years is the emergence of automotive Ethernet networks (alongside traditional CAN bus networks). Beyond changing vehicle architectures, automotive Ethernet is also shaking up the way OEMs and Tier 1 suppliers think about in-vehicle security.
To protect Ethernet in-vehicle networks and ECUs from growing cyber threats and to comply with new industry regulations, many automakers have elected to deploy intrusion detection and prevention systems (IDPS).
Let’s explore the reasons behind the transition to Ethernet networks and its implications for automotive security design, as well as reviewing best practices for implementing IDPS within a vehicle network.
The Need for Speed
After years of using the different variants of CAN bus as the almost-exclusive in-vehicle network type, many OEMs are moving towards hybrid in-vehicle networks that comprise both Ethernet and traditional CAN bus networks.
There are several factors behind this transition, and they’re all related to the need for faster data processing. The growth in sensors, cameras and the emergence of autonomous driving functionality dictate the transfer of complex data at higher throughput rates. Autonomous vehicles, for example, require high-performance computing to make decisions in real-time that profoundly affect the safety and lives of passengers and pedestrians.
Despite their reliability, CAN networks are limited in bandwidth and cannot deliver the throughput needed for today’s new applications. CAN networks can typically deliver up to 5 Mbps, while new Ethernet networks are already supporting a throughput of 1 Gbps. This huge upgrade, enabling wideband communication within the vehicle network, sparked the transition to automotive Ethernet a few years ago.
That’s not to say that CAN is going to disappear. CAN is a reliable and low-cost solution for certain types of ECUs. In terms of logic, CAN networks operate on a bus (one-to-many/broadcast communications), while Ethernet is more suited for point-to-point communications. For these and other reasons, CAN and Ethernet will most likely continue to operate side-by-side in modern vehicle architectures.
Don’t Confuse Automotive Ethernet with Your Office LAN
The Ethernet protocol has been commonly used in IT networks in offices and homes for more than 30 years. But automotive Ethernet networks are substantially different than your office LAN.
In the IT world, networks are constantly changing. People connect and disconnect many different devices (e.g., phone, laptop) and different apps on a frequent, ongoing basis. This means the network needs to support dynamic operations using, for example, dynamic IP address allocation, additional protocols and ports.
In vehicles, most network components are known (e.g., switches, ECUs, protocols, etc.) before you even connect them to the network. This allows automakers to structure the network and define static IP addresses, ports and even to specify the messages between ECUs, before the network is even physically connected.
Sample Automotive Ethernet Network
To understand what this looks like in a typical vehicle architecture, consider the following example.
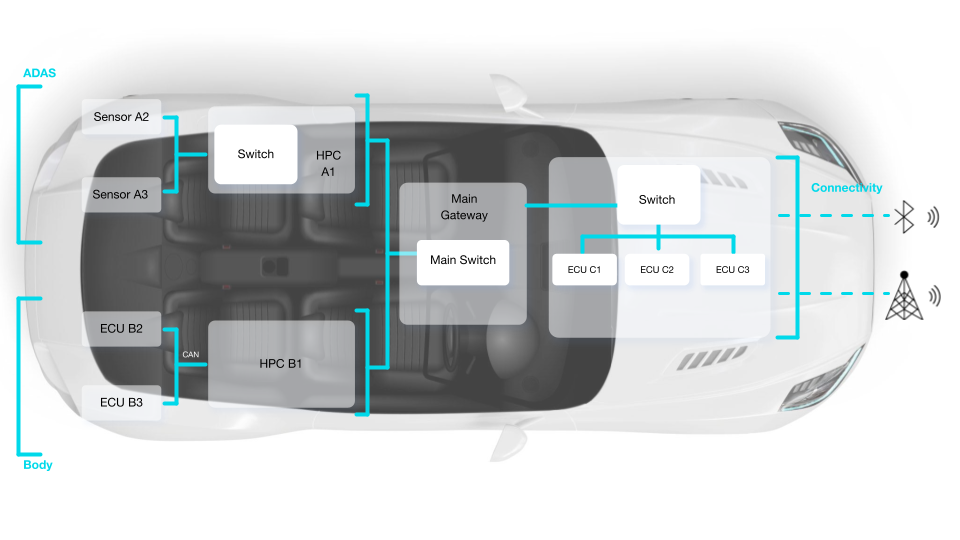
For reference, this hybrid vehicle network can be divided into three domains (ADAS, body, and connectivity) that are connected via a centralized Ethernet gateway. Ethernet traffic from sensors (A2 and A3) and CAN traffic from ECUs (B2 and B3) are being sent through high-performance computers (HPCs). These HPCs are connected via Ethernet to the main gateway responsible for routing traffic between domains. Communication ECUs (C1-C3) connected to the outside world (cellular, WIFI) are also sending Ethernet traffic to the main switch.
From a security standpoint, the question is how to protect such a connected vehicle network from malicious and unauthorized traffic.
Drivers for Automotive Cybersecurity
Implementing cyber protection in automotive networks is driven by two main factors: security value and regulatory compliance.
As vehicles become more connected and software-driven, there is a growing need to protect them from cyber-attacks that are liable to affect critical vehicle functionality and functional safety (e.g., airbags, braking system, etc.), potentially endangering lives and resulting in expensive recalls.
AUTO ISAC, an industry-driven community to share and analyze intelligence about emerging cybersecurity risks to vehicles, has outlined the tactics and techniques commonly used by attackers to penetrate vehicle networks. The most common attacks include spoofing, denial of service, scanning, fuzzing and data manipulation. With respect to Ethernet networks, all attack types found in the IT world are also relevant for automotive.
Most of these network-level cyber attacks comprise the following stages:
- An attacker finds a vulnerability (via scanning or fuzzing) in connected ECUs.
- The attacker exploits the vulnerability to get remote access to the ECU and compromises it.
- The attacker then moves laterally within the in-vehicle network to compromise ECUs in other domains.
The cyber protection mechanism that should be applied in the network shall be able to detect the techniques used to execute these attacks – such as initial access (e.g., by HW access), the discovery of network elements (scanning), lateral movement, data collection, and exfiltration – and prevent potential damage to ECUs. an example of such a mechanism is the Automotive IDPS (intrusion detection and prevention system) which would be detailed described later on.
Compliance, Compliance, Compliance
The second driver for automotive IDPS is the need to comply with new industry regulations, such as UNR 155 and GB/T, that require OEMs to monitor incidents and risks to their vehicle fleets over the entire lifecycle. UNR 155 has already become a de facto standard in Europe and Japan. The next milestone will take place in July 2024, when all new and existing vehicle types will also be subject to UNR 155 type approval for cyber security.
Annex 5 of UNR 155 specifically requires mitigation of threats related to “vehicle communication channels,” such as message spoofing, unauthorized data manipulation and access, replay attacks, denial of service attacks and malicious internal messages (among others). While UNR 155 doesn’t call for the use of a specific tool, IDPS is ideal for detecting and mitigating these types of threats.
Protecting In-Vehicle Networks with Automotive IDPS
A common security tool in the IT world, IDPS (intrusion detection and prevention system) is used to monitor and analyze network traffic and prevent potential attacks on a network or its endpoints.
Automotive IDPS inspects in-vehicle traffic in real-time, detects and can possibly block malicious communication based on predefined rules. Since in-vehicle networks are based on known communications (e.g., pre-defined services, pre-defined video streams, pre-defined connections between ECUs), the inspection component knows exactly what type of traffic to allow (i.e., whitelist) – anything else is considered a bug or an attack.
The goal of automotive IDPS is to detect all attacks without false positives. The fact that traffic is well-defined and limited in type enables the use of predefined rules with zero (or negligible) false positives. This level of accuracy is important as it saves valuable bandwidth and resources within the vehicle network, which are free to carry out other important functions.
Where to Implement Automotive IDPS in Vehicle Networks?
Most automakers today understand the need for automotive IDPS. As IDPS can be implemented on any ECU, or only on the most compromised ECUs, the question is how to do inspection in the most efficient manner.
One option is to deploy the inspection component on each ECU. This means deploying multiple IDS instances (per the number of ECUs), which increases complexity, degrades ECU performance and requires multiple integrations. This option also undermines the key goals of automakers – to maximize efficiency and reduce costs. These goals can be achieved by minimizing the number of inspections needed to achieve the desired result. Clearly, it doesn’t make sense to check the traffic at every single point in the network.
A preferable and less costly alternative is to perform inspection at one or a few centralized locations, according to the complexity of the vehicle architecture. But the question is where? Based on our example, if you deploy IDPS solely on the main switch, you won’t be able to detect malicious traffic between sensors A2 and A3. In this example, the solution should be IDPS instances on each switch to cover all the Ethernet traffic. Thus, the IDPS location really depends on the particular vehicle architecture and how the packets are routed.
In addition, there are mechanisms in the switches themselves that can do part of the inspection. This technique has a smaller performance impact than deploying IDS on the switch and reduces the resources consumed from the switch for inspection. Leveraging this technique requires knowledge of how to configure the switches using the right logic, including setting of filters, rate limits, etc.
How to Efficiently Configure Your IDPS
Efficient configuration is essential for maximizing results and performance from your IDPS implementation. Keep in mind that not all users are cybersecurity experts, so it’s important to make the configuration process as easy and smooth as possible.
The arXML file contains most of the relevant information (e.g., ECU information, and ECUs communication, etc.) and definitions of the vehicle network. Generating the IDPS inspection logic (whitelists, blacklists, DPI, etc.) from this single source makes it easier to create the inspection configuration. Once you set the required parameters for generating IDPS configuration, most of the inspection can be done automatically.
Bottom Line
Automotive Ethernet is being used in connected and autonomous vehicles to provide the wideband communication necessary to support autonomous driving and other advanced applications. Not only is automotive Ethernet transforming vehicle architectures, it’s also changing the cybersecurity paradigm.
Vehicle manufacturers seeking to secure their fleets and comply with regulations are deploying IDPS solutions for their in-vehicle Ethernet networks. To ensure a successful and cost-effective IDPS implementation, OEMs must decide where to implement the intrusion component and how to configure it in the most efficient manner.
Authors:

Michal Frenkel, VP Products & Strategy, Argus Cyber Security
Michal holds a BSc degree in Computer Science from The Hebrew University and a master’s degree in Computer Science from Bar Ilan University. Throughout her career, Michal has led product lines in various fields including SaaS, vulnerability management, virtualization, and more.

Ran Ben Tzvi, IDPS Product Manager, Argus Cyber Security
Ran is a cybersecurity and networking expert with over a decade of experience in development and product management. Ran holds a B.Sc. in computer science from the Open University of Israel and is passionate about exploring new technologies and staying at the forefront of the cybersecurity industry


