Cyber Security ecosystem in the world of IoT & shared mobility
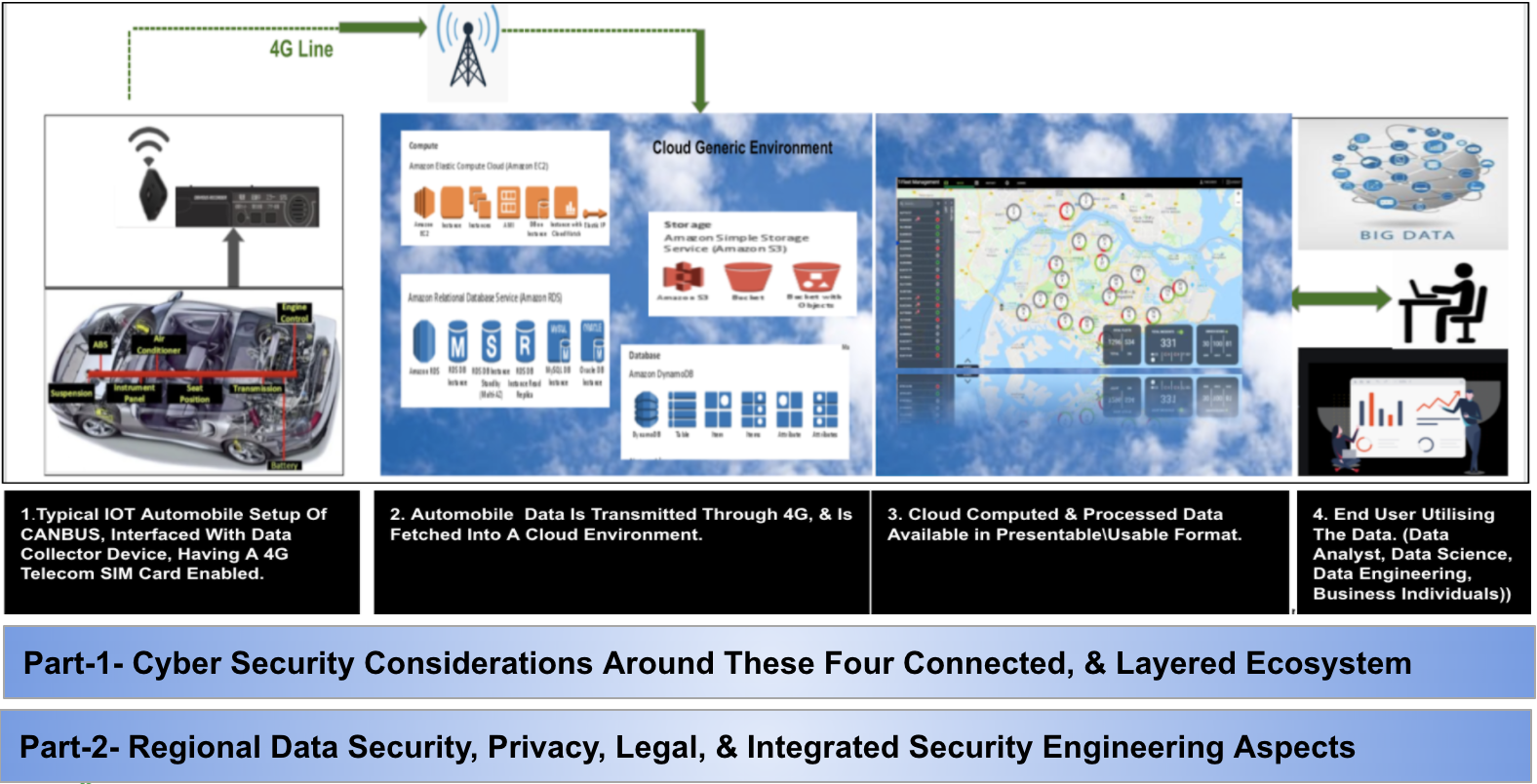
Different, heavy, and broader worlds are tightly affixed with each other, The IoT, Telecom, Cloud, BigData, the domain of shared mobility, & Cyber Security. Just an example case of say fleet management system of shared mobility, where a dedicated set of data is collected from a vehicle in real-time through IoT device, transferred to Cloud via Telco, this sensitive data gets cloud computed, processed, analyzed, stored, and used for various business reasons.

Head\Director of Engineering, Grab Group R&D
Well, so even before we go further, what can these datasets look like for the given example of saying renowned and globally operated fleet management organizations? So it can be divided into two sections:
A. Registered Drivers data (Name, Phone, Photo, Country-Identity Card, Driving Licenses, Email, and more..) B. Real-time Vehicle data (Geolocation, video, braking style, current speed, average speed, Engine on/off time, Engine idling time, Hard acceleration, Harsh braking, Sharp left/right Turns, Fuel consumption, Fuel levels, And more..) The sensitivity & importance of this data increases for a scattered business across the globe. And this data is collected say from various regions. Obviously, this will definitely be tagged as a BigData. Practically this data is owned by a specific business organization that is probably some automobile company. Or, an independent fleet management company. Applying appropriate data science and analytics, this particular case can generate us the combination of so many facts\patterns of drivers and vehicle usage. The number of business-sensitive problem statements can be predicted and solved in advance.
This case is pretty colorful now, we have personal data, as well as business-sensitive data. How if this data is stolen\breached through a Cyber Security attack and used by hackers?… If hacked\breached… can it be sold?…. Pheww….! The answer is simple, if not protected well, for sure, data will be breached, and based on its sensitivity, it can even get sold to the competitors. So let us have a quick dip into the cybersecurity ecosystem for a so far described connected world, and some primary areas to consider from the cybersecurity engineering controls which will make breach oriented conditions tuff to occur.
Securing Vehicle IoT Data Collection, hackers can extract and analyze electronic control unit (ECU) firmware. This allows for the discovery of possible vulnerabilities built into the firmware, as well as the extraction of sensitive data, such as encryption keys. This is the expected baseline assurance, to ensure that these files are protected and tamper-resistant is critical to overall system security.
Applying Cloud security covers the security of all the computing layers in public and private clouds. Apply tight security configurations for all cloud components\instances. Make sure we have appropriate EDR(Endpoint detection)\AMP(Antimalware protection) deployed across all instances. Better to have a brilliant vulnerability scanner running on all instances. Adopt golden image deployment with tight hardening, and automated patching capabilities. It is a must to have intelligent WAF (Web application Firewall) configured to protect applications, APIs, and mobile app backends against a variety of attacks including the OWASP Top 10, zero-day threats, data leakage, and application-layer denial of service (DoS) attacks. Having advanced bot protection with machine learning capabilities will provide bot spam detection, credential stuffing prevention, request risk scoring, and client fingerprinting.
Applying Cloud Application Security covers the security of cloud applications, making sure the application layer is safe. This type of security consists of properly programming cloud applications to avoid vulnerabilities such as SQL injection, cross-site scripting, weak authentication and session management, cross-site request forgery, etc. Automated, secure-SDLC is implemented across the
Incident response SOC for shared mobility with Fraud\Abuse Cases Detection We need to make sure here we have full-stack logs generated. Apart from regular cloud playbooks, with a special focus on defining mobility playbooks designed to block an attack targeted to a connected vehicle or mitigate potential risk. Mobility playbooks are completely different from enterprise playbooks where it usually involves assets like desktop, firewalls, etc. The mobility playbooks activate playbooks in the connected car’s environment and include unique workflows such as putting a vehicle or group of vehicles on quarantine, updating the drivers/passengers, controlling the OTA servers, etc.
Identity is a very border topic, in this context it is all about controlling the organization’s information in cloud applications by applying the right authentication & authorization mechanism. Well, it should effectively control who is uploading\downloading files, what documents have sensitive information, what documents are exposed to the Internet, and several other aspects. A focal point to consider is considering the right solutions and the right protocols(OAuth, SAML, LDAP, OpenID, etc) for various assets\entities which this ecosystem with Identify all the way from an in-vehicle device to right data file is accessed by the end-user.
About the author
Aniket Kulkarni is the security engineering leader at Grab group-Singapore and a founder member of Grab’s Infosec team. He is Heading\Directing bunch of Cybersecurity initiatives mainly inclined towards Cloud Application Security, Security Architecture, Regional data security and governance, Deals & Partnership Security focusing on southeast Asian countries giving legal, privacy angles for cross border data transfers.
Published in Telematics Wire