Protecting Connected Vehicles through Open Innovation

The connected car revolution has greatly accelerated in the past year and is expected to boost by end of 2023, with some 100 million vehicles on the road.
As OEMs are adapting massive digitalization and connectivity the vehicle architecture has become far more complex and consequently, the attack surface has significantly expanded.
Protecting against cyber threats has become mandatory to ensure the safety of cars, drivers and passengers, as well as to enable the adaption of new automotive technologies. This is a one of the focus areas of the Alliance Innovation Lab in Tel Aviv.
Connected Cars – The Core of the New Smart Mobility
A Connected Vehicle is basically connected to a network, that enables services such as: Vehicle tracking, Vehicle Diagnostic and Predictive Maintenance, Data-driven services like adapted insurances to the drivers’ behavior, online services or offers and incentives to the passengers through the infotainment unit, fleets management tools, and all sorts of data monetization possibilities from cars. In the future, at its highest level of connectivity, applications in the car could include a virtual companion or even chauffeur based on cognitive AI, with a high degree of personalized riding experience for all passengers in the car. Connectivity and communication between the car and its environment (V2X), is also an important enabler for autonomous driving,
This connectivity is supplied through the TCU (Telematic Unit) or In-Vehicle Applications. The TCU “listens” to the bus in order to extract relevant data out of it, mainly data that had been configured before. As the TCU is an embedded part in the on-board architecture it has the capability to transfer the information from the vehicle outside (to the Cloud) and from outside to the vehicle.
Vehicles can be connected using Aftermarket tools (OBD-II, GPS Tracker for Fleet Management, etc.) or Original set-up from the vehicle OEM (Software or Hardware).
The components used in connected vehicles are: TCU, Infotainment Unit, Driver Assistant Unit, and V2X, while the connected vehicle interfaces (Entry-points) would be Bluetooth, Wi-fi, Cellular network, GPS, OBD-II, 1/2 din-dash, Sensors (such as TPSM), Lidar and Camera, Keyless entry.
Remote Attacks vs Physical Attacks
The connected vehicle exposed the OEMs to a wider scope of new entry points for the attacker to manipulate. Remote attacks seem to have higher stake than the physical attacks, since in a physical attack the attacker would need a physical access, which reduces the risk.
We already saw remote manipulations (For example: Jeep Cherokee) that can cause a real impact on the vehicle, driver, etc.
CAN bus protocol – Secure or Unsecure?
CAN bus is based on a broadcast protocol divided into 2 wires – CAN-H and CAN-L, where information can be transmitted and received from ECUs connected to the network.
In the CAN network we can find ECUs, TCUs and Gateway. The CAN network is divided into subnetworks that are connected to the Gateway.
Since the CAN bus protocol is based on message broadcast system it involves some issues related to security. Therefore, some of the OEM’s shift to other protocols such as Ethernet, but still, most of the OEM’s use CAN bus or a combination of protocols.
An example of the security issues within the CAN bus protocol:
- There is no authentication mechanism – DDOS , Tampering and poisoning attacks are more than welcome
- Lack of encryption – Every ECU connected to the same bus can sniff the entire messages running on the same bus.
- Lack in MSD (Message Source Detection) – it is not possible to know if an ECU sends or receives any message
How to mitigate the lack of security in the CAN bus protocol?
- Encryption
- Firewall
- Message Authentication
- Message Source Detection
- Intrusion detection/Prevention Systems
- Host-based / Gateway
- Deterministic
- Heuristic
- Host-based / Gateway
- HSM
There are still some limitations to mitigate the risk due to latency, behavior, computing power, false positive ,cost and you need to take into account that only by protecting the CAN bus you are not protecting the full scope of connected vehicles.
Cybersecurity – a mandatory transformation
The Alliance Innovation Lab Tel Aviv aims to advance the state-of-the-art mobility, with a main focus on vision sensors, data & AI, and Cybersecurity. The latter is seen as an enabler for the integration of any other new technologies. Through collaborations with innovative Israeli startups, our mission is to identify and test technologies that could be implemented in future cars and services offered by the Alliance member companies. As part of our open innovation approach, the Lab collaborates with the local innovation ecosystem through joint prototyping efforts (POC). To date it has led more than 20 collaborative projects with Israeli start-ups, some of them are in Cybersecurity, being one of Israel’s strongest tech domains.
These collaborations roll out as the automotive industry prepares for the new UN Regulations set to come out in January 2021, which require car manufacturers to secure connected cars from cyber-attacks. (Ref: https://www.unece.org/info/media/presscurrent-press-h/transport/2020/un-regulations-on-cybersecurity-and-software-updates-to-pave-the-way-for-mass-roll-out-of-connected-vehicles/doc.html) .
In light of all the above, managing software security is no longer an optional activity for car manufacturers but a mandatory transformation to a future with fully automated, self-assessed, self-healing software
This means that OEM’s, as well as Tier1’s and other suppliers will now need to enforce the following steps in order to mitigate the risk from the supply-Chain through the Value-Chain:
- Cyber Security Risk Management
- Security by Design
- Detection & Response
- Secure Updates
To address the new regulation the OEM’s are adding some layers to enrich their capabilities:
- In-Vehicle Security solutions
- Cloud solutions – for E2E visibility & detection on the connected Apps to the connected Vehicle
- ASOC – Automotive Security Operation Center
- Validation and Risk management solutions
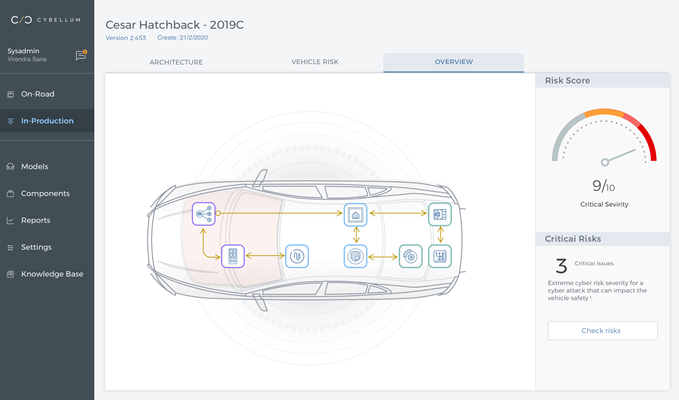
The first vehicle-level automated risk assessment solution
Cybellum Israeli startup is a leader in Automotive Cybersecurity Risk Assessment. Our team at Renault Nissan Mitsubishi Innovation Lab collaborates with Cybellum to offer innovative vulnerability detection for vehicles’ software, developing the first vehicle-level automated risk assessment solution.
This strategic cooperation is the first in the world to focus on vehicle-level risk assessment
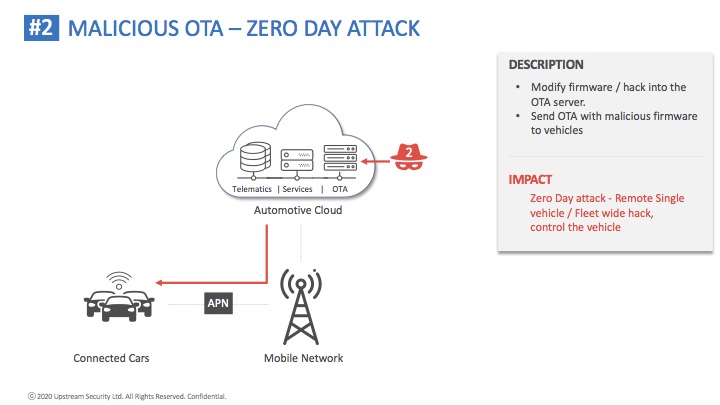
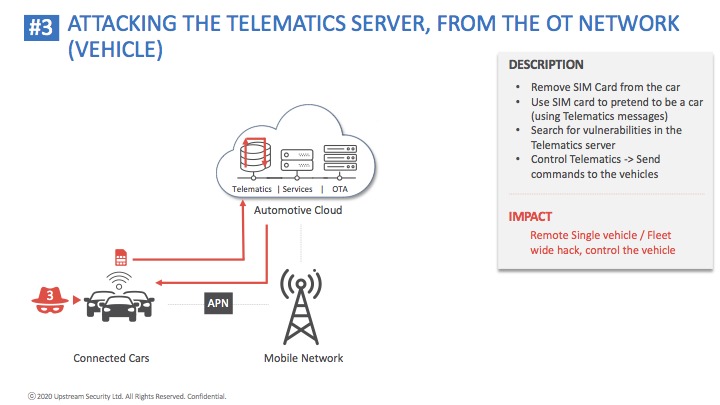
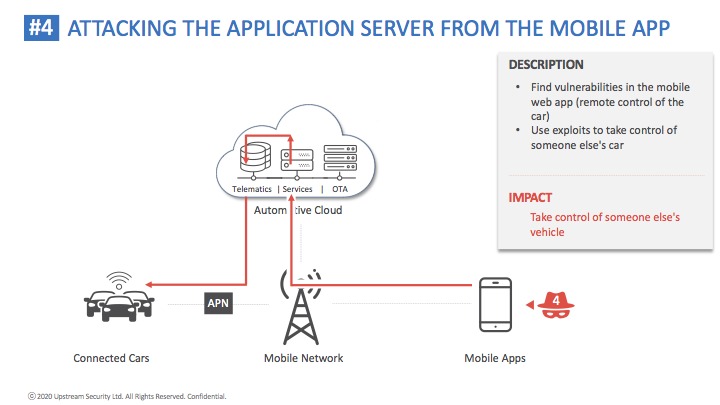
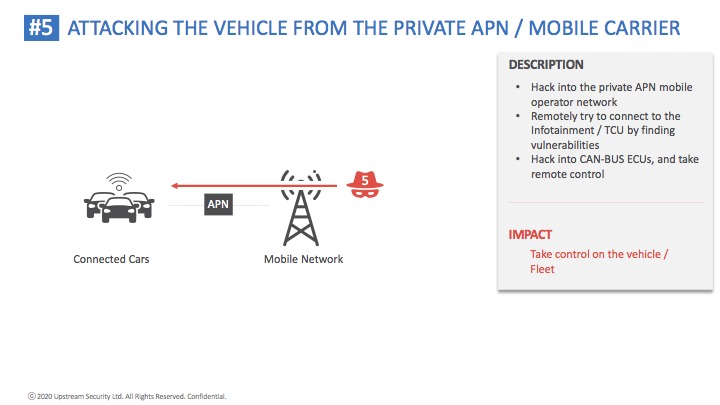
Cybellum solution enables automotive OEMs and suppliers to identify and remediate security risks at scale, throughout the entire vehicle life cycle. Their agentless solution scans embedded software components without needing access to their source code, exposing all cyber vulnerabilities. Manufacturers can then take immediate actions and eliminate any cyber risk in the development and production process, before any harm is done, while continuously monitor for emerging threats impacting vehicles on the road.
Following a successful POC of Cybellum’s solution, done by the Innovation Lab, we cooperate to build innovative cybersecurity technologies to be implemented in the automotive market.
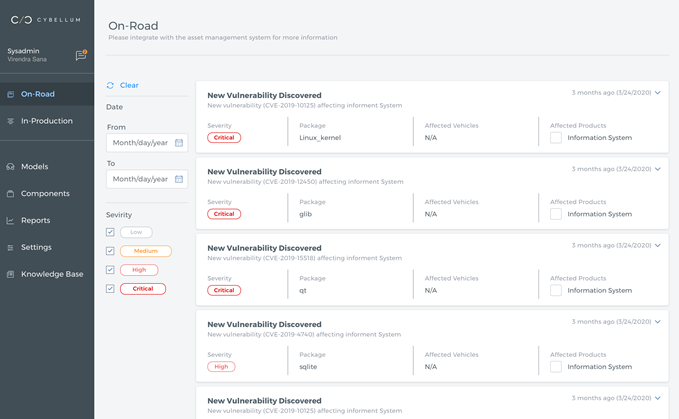
Today, most of the risk assessment in the automotive industry is conducted manually or using tools on a single component level. This methodology cannot scale and only provides partial information. An entire vehicle is a very complex system composed of over a hundred connected components, with a complex interconnection.
Our cooperation focuses on vehicle-level risk assessment, taking into account the architecture of the vehicle model and the automated assessment of a vehicle’s complex mesh of software and hardware. Together we aim to bring to the market the first solution that can calculate the risk of a vulnerability in the full vehicle context, help the Alliance brands to manage the risk accurately, save time and be competitively prepared for upcoming regulations.
Cybellum automotive risk analysis solutions automatically detect a wide range of vulnerabilities in in-vehicle ECUs and other automotive software. Using upcoming developments from the new cooperation, Alliance companies will be able to use the Cybellum solution suite to gain full, ongoing visibility to their cybersecurity exposure at the vehicle level and get the necessary guidance on risk remediation.
A successful collaboration with Upstream Security to mitigate connectivity risks
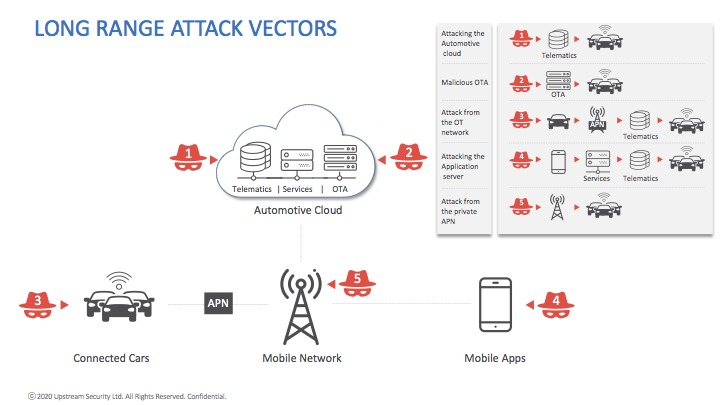
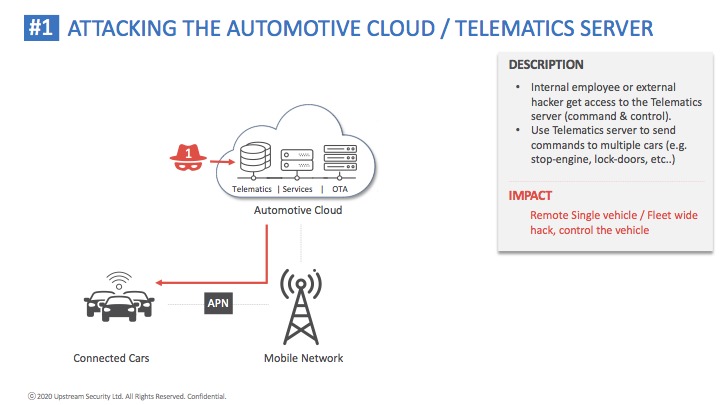
Upstream helps corporations mitigate connectivity risks and ensure the safety and security of smart mobility solutions protecting connected and autonomous vehicles, SAE levels 0-5, from remote cyber attacks generated over the public internet or private mobile APN, as well as from fleet-wide attacks targeting multiple vehicles at the same time. Their team has developed a comprehensive protection of the mobility service infrastructure, connected vehicles and the people inside them.
Over the past year, Alliance Innovation Lab Tel Aviv worked together with Upstream Security to design a cybersecurity solution for connected cars within the Renault- Nissan-Mitsubishi Alliance. As part of the effort, market research, technological evaluations, and business evaluations took place. The rigorous and in-depth joint PoC subsequently found that Upstream’s solutions seamlessly fit the Alliance’s cybersecurity and business needs.
The Alliance Innovation Lab and Upstream collaborative journey started after a scouting process where we found Upstream Security to offer the most mature end-to-end cybersecurity solution covering telematic servers, mobile applications, and the car itself.
The Lab approached Upstream with a long list of requirements for a solution that would improve our cybersecurity posture. Among the features that were requested were: no in-vehicle installation and therefore quick deployment and no impact on vehicle production cycles, a product with a proven track record that was already tested, verified, and in production, and finally a solution that would match the business needs and challenges of the Alliance members.
The year-long three-part confirmation process included a solution landscape evaluation, a technical evaluation and PoC using the Lab’s cybersecurity research team and the Lab vehicles, and lastly, a business evaluation, where the business and the commercial potential of Upstream’s solution was evaluated in accordance with the Alliance members’ needs.
After an in-depth discussion, Upstream was found to be worthy of more than just a successful POC, and Alliance Ventures, the Alliance corporate venture capital fund invested into Upstream, leading its $30M series B of financing.
As the automotive world moves toward electric, connected, and autonomous vehicles, it leads to good opportunities, but also to risks. The industry are looking for cyber protection for cars and services, not only in the car, but also at the communication and cloud level. After seeing the success of the collaborative efforts, both the Alliance Innovation Lab and Upstream Security are committed to continue joining forces to make the future of smart mobility safer and more secure.
Author:
As part of his role, he manages the Lab’s relationship with Israeli startups in the field of automotive cybersecurity, including scouting and evaluating companies through feasibility tests and prototyping efforts (POC).
Raziel brings 15 years of experience in cyber positions starting in in Rafael, Unitask, National Bank and other financial and technological entities. He is a graduate of MAMRAM, the IDF Computer Center and Information Systems.
Published in Telematics Wire




