Cybersecurity Assessment for EV Ecosystem – End-to-End Approach

The emergence of electric vehicles (EVs) is helping reduce carbon emissions by driving a shift away from fossil-fuel burring vehicles. A consequent aim of enabling a higher number of people adopting EVs depends on not only the easy availability of charging infrastructure but also on the overall reliability of the EV ecosystem.
An implementation of EV Infra helps create connections between transportation systems and electrical grid – a phenomenon that is not common with users in a gasoline-powered vehicle environment. Researchers agree that new targets for attackers and the potential for new vulnerabilities have been created with the rise of this connected ecosystem.
The security of the information lying in the EV or EV Charging system is a mandatory requirement for all EV participants to be accepted widely. From an attacker perspective, it is important to understand each step of the process before executing the attack, because targeting such highly sophisticated system requires a high level of expertise of the process itself.
The automotive cybersecurity environment is dynamic and is expected to continuously change over coming years. With the global automotive sector moving toward a software defined vehicle paradigm, the information revolving in and around the vehicle become an important factor. This has enabled attackers to exploit and use these new features for malicious intents.
2021 saw 56.9% of attacks carried out by black-hat actors, up from 49.3% in 2020[4].
The Challenges of the EV Ecosystem: A Cybersecurity Perspective
Currently, the key challenges of the industry with respect to EV Cybersecurity center around:
- No comprehensive cybersecurity approaches for EV scope,
- Limited best practices as a standard, and
- Inadequate understanding of the attack surfaces, interconnected assets, and unsecured interfaces.
A significant number of cyber-Software-Physical components are part of this ecosystem.
While inside the EV vehicle, EV onboard chargers comprise of Battery Electronic Control Module with Battery Management System. On the other hand, an EV charging station comprises of the Off-board EV Controller with the Backend system. The scope of this system is huge, and many standards can be introduced to create custom frameworks, hence, the breadth of the current study has been restricted to achievable targets.
Electric Vehicle Supply Equipment (EVSE) is a relatively new infrastructure and multiple researchers pointed out the lack of understanding of the risks and necessary controls. As a result, significant attention and efforts are being devoted to the development of threat models.
Reliable threat models are needed to help determine what risks exist and what controls might mitigate such challenges. Without threat models, it is difficult for manufacturers, users, and the Government and regulatory authorities to make risk-based decisions on the controls needed.
To articulate the requirement, a security professional must first ask questions. These questions (in the below table) are the first step of defining the items, a well-known process in the ISO/SAE 21434, helping recognize the scope of the project.
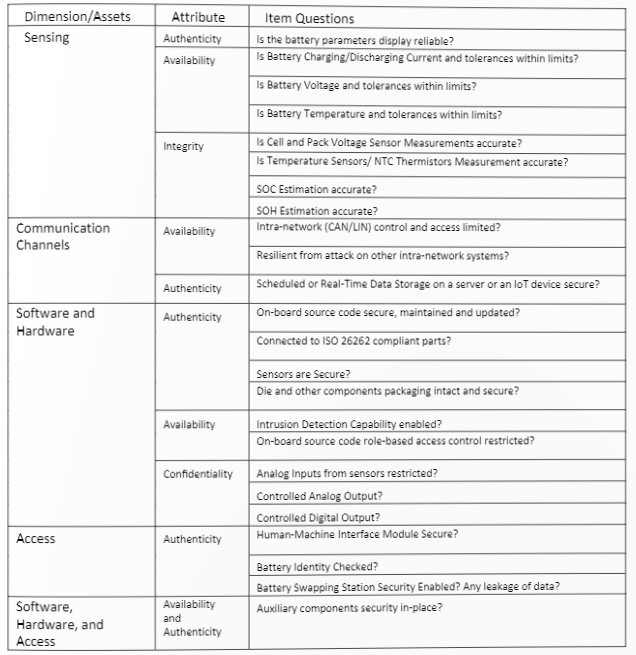
The ISO/SAE 21434 standard relates to components, spare parts, and accessories for production vehicles. Practitioners might argue that infrastructure outside the vehicle is not actually covered by the standard.
However, in order to protect the cyber ecosystem and reduce the cyber risks from attacks, it is necessary to formulate prevention plans for the charging infrastructure as a linked part of e-vehicle infrastructure. A security-oriented mindset is essential here.
However, in such complex architecture of network, software, and cloud infrastructure, ISO/SAE 21434 alone cannot cover all the pillars.
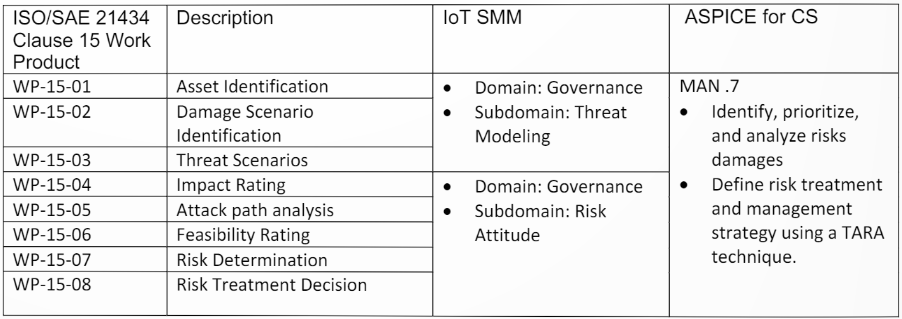
A customized framework provides the necessary guidance to cover all aspects of product and service security in the defined use case. ISO/SAE 21434 defines different clauses to cover the vehicle cybersecurity, whereas IoT SMM and ASPICE covers the EV ecosystem and Software Development scenarios. It is important to correlate the TARA process and Reports, which can be used by the cybersecurity experts and the monitoring team in PSIRT, and the Project teams to cover the whole lifecycle of the project.
The framework suggests use of TARA (Threat Analysis and Risk Assessment) methodology in the EV ecosystem and discover and document the cybersecurity risks, instead of limiting it to the vehicle level. A similar approach can be taken to produce and identify gaps in the EV charging Platform hosted in Cloud, mapping with WP.29(R155 and R156) regulations.
In ISO/SAE 21434, Cybersecurity assurance levels (CAL1,2,3,4) and methods to arrive on assurance levels. There is no doubt that this standard is complex, however, It provides ample facility for the implementers to identify the cyber security maturity levels and define strategies accordingly. This will simplify the cybersecurity implementation activities and help them to manage the system in an effective way. A detailed IoT SMM Practice and ISO 21434 section wise mapping to be established with relevant Compressive level. Similarly, relevant cloud and application security benchmarking process to be adopted and mapped with this framework for assessment of the backend Infra and hosting platform. OWASP, MITRE. A similar approach can be taken for Electrical/Electronic assessment of EV Charging module with UL 2202, UL2504 etc. for EVSE certification.
The table below provides a mapping between different Standards in discussion. IoT Security Maturity Model which provides a strong industry accepted guidance to reach desired the desired maturity level. This is especially true since the EV ecosystem is nothing but a large domain centric IoT System, and IoT SMM provides an overall guidance to reach the target level of maturity.
Charting the Future: Driving Reliability and Trust
The increasing popularity of electric vehicles has prompted Governments to fund the growing demand for electric vehicle charging stations across the world. However, these stations may pose an invisible danger. Since all EVs are going to connect to national PowerGrid via these Charging Stations, so a bad-actor EV could be enough to bring down the power distribution system of a country.
According to industry experts, while EVs are now protected to an extent via regulations, public EV chargers are still vulnerable against physical attacks and could easily be used in the same way hackers target ATM machines to steal data.
Public EV charging is mostly enabled through the Open Charge Point Protocol (OCPP). OCPP coordinates communication and power flow between charging points, control center, the EVs and the grid. OCCPv1.6, by design, introduces several threats to the EV public charging system. These threats arise from the fact that OCCP communicates information in clear text.
However, in the presence of TLS, OCPP is subject to impersonation attacks where an attacker pretends to be charging participant, to request or acquire private data regarding the charging transactions performed by the different EVs.
Here is a sample list of potential threat scenarios that may occur to different components in the EV backend Infrastructure.
| Sl. No. | UNECE Reference | Asset/Components | Risk assessment analysis | Attack Vector (STRIDE) | Impact (CIA) | Expected damage Scenario | Risk Level |
| 1 | R155 | Network Channel between Mobile, Charge Point App and APP GW | The attacker manipulates request/ response data | Tampering | Integrity | False data may be delivered to the user | High |
| 2 | R155 | EVSE APP GW | Attacker manipulates routing config and deny manipulation | Repudiation | Integrity, Availability | Attacker may manipulate and deny change of routing configuration | Medium |
| 3 | R155 | EVSE Micro-Service Gateway | Attacker sniffs safety and security critical data on communication channel | Information disclosure | Confidentiality | Attacker may sniff personal and safety related data of the user or vehicle and attempt to impersonate user | High |
| 4 | R155 | EVSE DB server | Attacker sniffs safety and security critical data on communication channel | Information disclosure | Confidentiality | Attacker may sniff personal and safety related data of the user or vehicle and attempt to impersonate user | Medium |
| 5 | R155 | DSO Services | External attacker accesses data from a different user/ admin. | Escalation of privilege | Confidentiality | External attacker may access confidential data of other users/ admin | High |
| 6 | R155 | Cloud VPN Gateway | External attacker sends multiple packets to the same service causing delay and failure in processing requests. | Denial of service | Availability | External attacker may overload service due to lack of rate limiting causing Denial of Service | High |
| 7 | R155 | EVSE Services | External attacker may attempt to brute force authentication | Spoofing | Confidentiality | External attacker may gain access to API without valid credentials | High |
| 8 | R156 | CPO Server | External attacker attempts to connect to CPO VM | Elevation of privilege | Confidentiality | Attacker is able to access VM local data files, services and host a connection over the internet | High |
| 9 | R156 | CPO Server | Attacker sniffs channel used for firmware transfer | Information disclosure | Confidentiality | Attacker is able to capture firmware transfer over network | High |
| 10 | R156 | CPO Server | Attacker flood communication channel | Denial of Service | Availability | CPO services deny firmware update request from vehicle(s) | High |
| 11 | R156 | CPO Server | Attacker abuses firewall config to attempt SSRF | Spoofing | Integrity | SSRF allowing attacker to gain access to local and remote files | High |
ISO 15118-2 specification creates the requirements for the network and application protocol layers of the V2G communication interface between the EV, the EVSE, and one or more Secondary Actors (SAs). The ISO 15118 PKI that provides the authentication Certificates is anchored by the V2G Root CA[3]. This requires framework to assess the attack vectors to this certificate management system which is part of EV Backend Infrastructure.
We are proposing that the ISO/SAE 21434 standard be adopted as a base for Assessment approach and be mapped with various best practices from IoT, cloud and software processes to make it robust. The framework covers every phase of the life cycle of EV and EV infrastructure – from development through incident response to discontinuation. It also requires cyber security methods to be applied to all electronic systems, components, software, and all external connections.
The custom framework built to cover cyber security would also be applicable throughout the supply chain. The individual standards mapped in the proposed framework are not exclusive, and we can add other relevant standards to cover every potential cybersecurity vulnerability based on use cases.
The primary goal of the cybersecurity assessment is therefore not just to comply with a given checklist, but think like a hacker and fill in the security gaps for driving reliability and trust.
References:
[1] ASHWIN CHANDWANI, SAIKAT DEY , AND AYAN MALLIK(Member, IEEE), “Cybersecurity of Onboard Charging Systems for Electric Vehicles_Review, Challenges and Countermeasures”, December 31, 2020.
[2] Devin Reeh, Francisco Cruz Tapia, Yu-Wei Chung, Behnam Khaki, Chicheng Chu, and Rajit Gadh,
“Vulnerability Analysis and Risk Assessment of EV Charging System under Cyber-Physical Threats”
[3] Jay Johnson, Benjamin Anderson, Brian Wright, Jimmy Quiroz, Timothy Berg, Russell Graves, Josh Daley, Kandy Phan, Michael Kunz (Sandia National Laboratories) Rick Pratt, Tom Carroll, Lori Ross O’Neil, Brian Dindlebeck, Patrick Maloney, James O’Brien, David Gotthold(Pacific Northwest National Laboratory), Roland Varriale, Ted Bohn, and Keith Hardy (Argonne National Laboratory), “Cybersecurity for Electric Vehicle Charging Infrastructure”
[4] https://upstream.auto/h12022-automotive-cyber-trend-report/
Authors:

Atanu Niyogi
Cyber Security Head
L&T Technology Services Limited
With an experience spanning 18+ years, Atanu Niyogi has worked as delivery head and Technical architect on a number of IoT, Cloud and analytics projects. In his current role, as Cyber Security Head, he helps enterprises build robust cyber security strategy. Atanu is an expert in IoT security and has a strong interest in building Product and OT security and solutions.

Sudip Pramanik
Technology Lead
L&T Technology Services Limited
With 14+ years of experience, Sudip Pramanik pursuing Master’s in Smart, Connected and Autonomous Vehicles from University of Warwick, UK. He is a Computer Science graduate and M.Tech in Automotive Electronics. Currently, he is associated with the Digital Products and Services unit of L&T Technology Services as Cybersecurity Specialist, serving Cloud, IoT and Automotive cybersecurity demands.
Published in Telematics Wire