Automotive cybersecurity: The future of EV charging stations

The connected vehicle ecosystem bringing in highly complex manned and unmanned infrastructure. It is important to enable this infrastructure user-convenient and secure to offer reliable services.
The automotive industry is evolving continuously where electricity will be a new fuel to these moving objects. We are living in a fast-paced technological era where our vehicles are supposed to store power packs securely, faster than ever. At the same time, it is vital to ensure safety of car occupants having cybersecurity measures in place.
V2G – Vehicle to Grid communication
A modern electric vehicle requires a fast charging infrastructure, which is possible through power line communication (PLC). It can fully charge vehicle battery very quickly having IP stack on top of it to carry power packs and to make payments automatically, based on power consumption. V2G will allow vehicle to communicate with external world, which is charging station. This topology poses several cybersecurity threats to the vehicle.
ISO 15118 is an international standard outlines digital communication between an electric vehicle and charging station, to charge EV’s high voltage battery. ISO 15118 offers standard practices for information exchange through different parts. The link between electric vehicle and grid must be secure to exchange private and payment related information to maintain confidentiality, integrity, and availability. This process is also known as plug and charge where mutual authentication to payment processes done automatically.
V2G implementation should have well planned cybersecurity measures in place to achieve CIA along with identity, authentication, authorization and accountability.
Threats taxonomy for Vehicle-to-Grid power communication
Here are some possible threats including impersonation, stealing payment related information, tampering with communication messages, eavesdropping, denial of service (DoS) and privacy breaches.
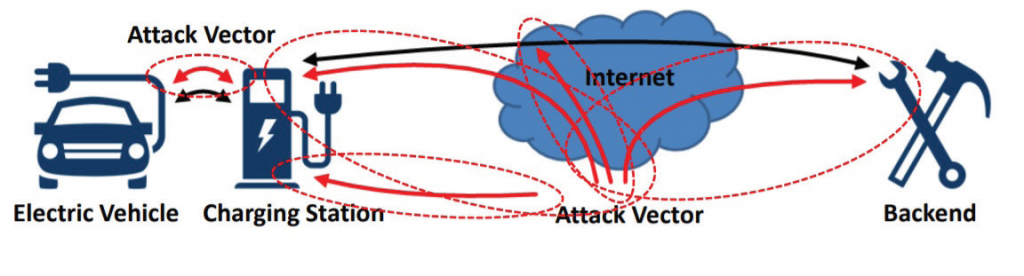
- Vehicle Threats – In V2G communication, an adversary can impersonate as a charging station to communicate and make harm to vehicle ECU. This includes tampering firmware on vehicle ECU that has onboard port for charging gun. This attack can also enable an adversary to tamper with calibration files, vehicle gateway logic, and steal sensitive information.
- Exchanged Information Leakage – In plug and charge, infrastructure there is lot of private information being exchanged with the charging station that can be compromised. The IP stack, if not protected, leaves data in clear to the impersonated adversary. This information may include credit card information, vehicle digital identification numbers, and EV battery specific data.
- EV Charging Station Threats – The charging stations are the endpoint to the power grids operated by charging point operators (CPO). Tampering with the charging station may lead to metering, business logic and access to backend infrastructure through charging station. The external devices can impersonate as a vehicle and try to infect EV charging station.
Cybersecurity measures in V2G
The power grid is a critical infrastructure and every device that connects to the grid, including EVs and charging stations, needs to provide measures to protect the grid from potential attacks. Imagine the loss of user trust in the charging infrastructure if third parties could manipulate massive amounts of charging-related information and billing data from a charging process.
Successful plug and charge infrastructure must be able to provide,
- Encryption and decryption of messages to ensure adversary is not able to eavesdrop on the channel to ensure confidentiality.
- Verify the integrity of information exchanged.
- Verify the communication party (EV or charging point) who it claims to be, in order to ensure authenticity.
Trust model in V2G
To establish trust model in V2G infrastructure, it is important to deploy robust public key infrastructure (PKI). Public Key Infrastructure (PKI) is a hierarchical structure of trusted third parties known as certificate authority (CA). The primary responsibility of CA is to manage the cryptographic keys used in PKI along with issuance, storage, distribution and revocation of digital certificates. The digital certificates are also known as public key certificates. A digital certificate is used for verification where vehicle can verify charging station and vice a versa, during handshake, before both the nodes start exchanging information. What if fake certificate is presented in this communication? Yes, to avoid any such situation vehicle and charging station should have integration with CRL to verify if the certificate issued by CA is still valid or not. There can be other relationship based trust model in PKI that can help to verify the digital certificates.
TLS stack on the power line communication (PLC) should support strong cipher suites supporting confidentiality, integrity and authenticity. It is important to understand the need of strong protocol (TLS 1.2) and algorithms power line to avoid data compromise.
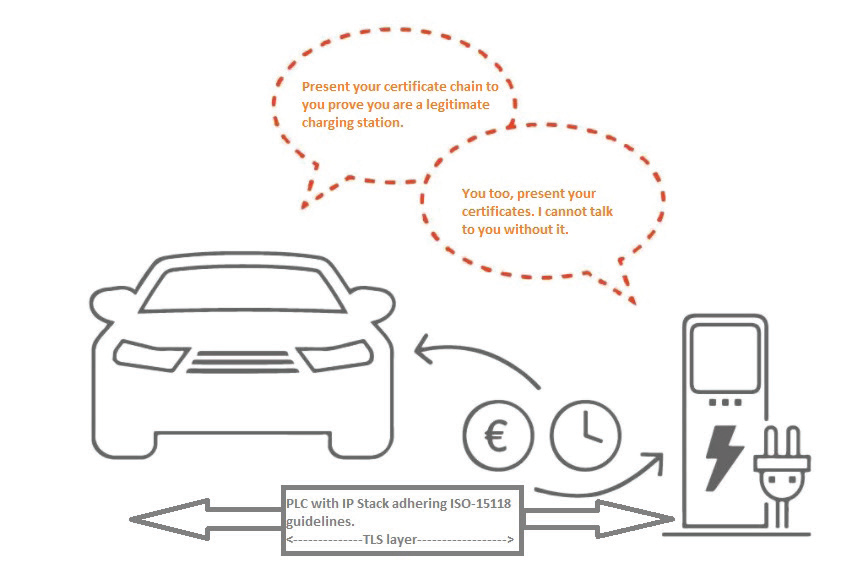
ISO 15118 recommends using digital certificates to authenticate and authorize access to charging stations and electric vehicles. The vehicle OEMs and charge point operators must establish sub-CA to issue digital certificates for this purpose. It is highly recommend managing cryptographic keys life cycle in HSMs at the backend to avoid compromise.
The vehicle manufacturer and charge point operator must provide mechanisms to revoke and renew the certificates in case cryptographic keys compromised.
Conclusion
The compromised V2G infrastructure not only endanger vehicle and grids but also attract penalties/fine for loosing data privacy. All in all vehicle OEMs and charging station manufacturers may have huge financial impact depending on regional legislation. In automotive industry, UNECE WP.29 cybersecurity regulation is a game changer. Several countries have already committed to automotive cybersecurity adherence for new vehicle launch and other countries still have time to build cybersecurity organization. It is highly recommended to start small with vehicle/infrastructure security assessment and based on risk appetite manage the cybersecurity risks.
Author:
A cybersecurity professional with 17+ years of experience in embedded security, applications security, cloud security, cryptography, and hardware security modules. Primarily focused on cybersecurity training and consultancy to the OEMs, Tier-I and Tier-II. IoT security for automotive and energy sectors is the current area of focus.
Published in Telematics Wire






Hi Kuldeep
Good day,
Usually, most of the readers do not post comments and appreciate the value of content and unfrotunately I am also one of them but after reading your article I must say that the way you have simplify and explained V2G cybersecurity measures in easy lanaguage made me to express the gratitude and appreciate your contribution to the knowledge.
Thank you very much for your great work.
Regards
Afan Rauf