Autonomous Vehicle
An autonomous car is a vehicle capable of sensing its environment and operating without human involvement. A human passenger is not required to take control of the vehicle at any time, nor is a human passenger required to be present in the vehicle at all. An autonomous car can go anywhere a traditional car goes and do everything that an experienced human driver does.
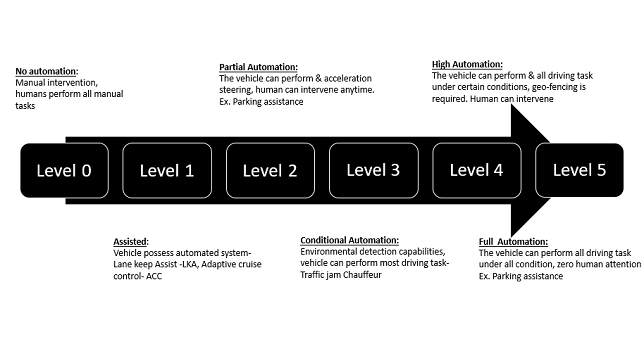
The Society of Automotive Engineers (SAE) currently defines 6 levels of driving automation ranging from Level 0 (fully manual) to Level 5 (fully autonomous). These levels have been adopted by the U.S. Department of Transportation
Level of autonomous vehicles:
Level 0- No driving automation:
Most vehicles on the road today are Level 0: manually controlled. The human provides the “dynamic driving task” although there may be systems in place to help the driver. An example would be the emergency braking system―since it technically doesn’t “drive” the vehicle, it does not qualify as automation
Level 1- Driver Assistance:
This is the lowest level of automation. The vehicle features a single automated system for driver assistance, such as steering or accelerating (cruise control). Adaptive cruise control, where the vehicle can be kept at a safe distance behind the next car, qualifies as Level 1 because the human driver monitors the other aspects of driving such as steering and braking.
Level 2- Partial Driving Automation:
This means advanced driver assistance systems or ADAS. The vehicle can control both steering and accelerating/decelerating. Here the automation falls short of self-driving because a human sits in the driver’s seat and can take control of the car at any time.
Level 3- Conditional driving automation:
Level 3 vehicles have “environmental detection” capabilities and can make informed decisions for themselves, such as accelerating past a slow-moving vehicle. But―they still require human override. The driver must remain alert and ready to take control if the system is unable to execute the task. features Traffic Jam Pilot, which combines a lidar scanner with advanced sensor fusion and processing power
Level 4- High Driving Automation:
Level 4 vehicles can operate in self-driving mode. But until legislation and infrastructure evolves, they can only do so within a limited area (usually an urban environment where top speeds reach an average of 30mph). This is known as geofencing. As such, most Level 4 vehicles in existence are geared toward ridesharing
Level 5 -Full Driving Automation:
Level 5 vehicles do not require human attention―the “dynamic driving task” is eliminated. Level 5 cars won’t even have steering wheels or acceleration/braking pedals. They will be free from geofencing, able to go anywhere and do anything that an experienced human driver can do. Fully autonomous cars are undergoing testing in several pockets of the world, but none are yet available to the general public.
Components required to build an autonomous vehicle:
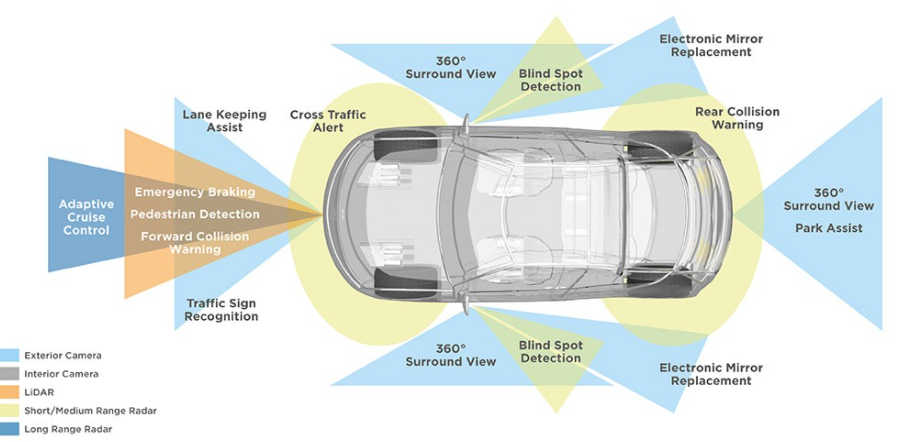
Challenges
Fully autonomous (Level 5) cars are undergoing testing in several pockets of the world, but none are yet available to the general public. We’re still years away from that. The challenges range from the technological and legislative to the environmental and philosophical. Here are just some of the unknowns.
Lidar and Radar
Lidar is expensive and is still trying to strike the right balance between range and resolution. If multiple autonomous cars were to drive on the same road, would their lidar signals interfere with one another? And if multiple radio frequencies are available, will the frequency range be enough to support mass production of autonomous cars?
Weather Conditions
What happens when an autonomous car drives in heavy precipitation? If there’s a layer of snow on the road, lane dividers disappear. How will the cameras and sensors track lane markings if the markings are obscured by water, oil, ice, or debris?
Traffic Conditions and Laws
Will autonomous cars have trouble in tunnels or on bridges? How will they do in bumper-to-bumper traffic? Will autonomous cars be relegated to a specific lane? Will they be granted carpool lane access? And what about the fleet of legacy cars still sharing the roadways for the next 20 or 30 years?
State vs. Federal Regulation
The regulatory process in the U.S. has recently shifted from federal guidance to state-by-state mandates for autonomous cars. Some states have even proposed a per-mile tax on autonomous vehicles to prevent the rise of “zombie cars” driving around without passengers. Lawmakers have also written bills proposing that all autonomous cars must be zero-emission vehicles and have a panic button installed. But are the laws going to be different from state to state? Will you be able to cross state lines with an autonomous car?
Accident Liability
Who is liable for accidents caused by an autonomous car? The manufacturer? The human passenger? The latest blueprints suggest that a fully autonomous Level 5 car will not have a dashboard or a steering wheel, so a human passenger would not even have the option to take control of the vehicle in an emergency.
Artificial vs. Emotional Intelligence
Human drivers rely on subtle cues and non-verbal communication—like making eye contact with pedestrians or reading the facial expressions and body language of other drivers—to make split-second judgment calls and predict behaviors. Will autonomous cars be able to replicate this connection? Will they have the same life-saving instincts as human drivers?
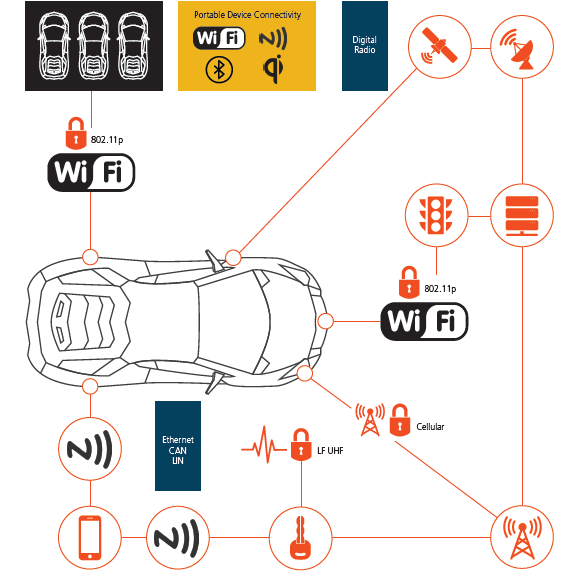
Connected Autonomous vehicle threat:
Remotely control a vehicle
Researchers have successfully demonstrated that it is possible to hack production vehicles from remote locations2 – allowing the attacker to take control of radio, windows and even brakes, acceleration and steering. There are many variations on this but the attack follows a similar pattern: an attacker exploits a vulnerability in a cellular system and lands on the vehicle’s infotainment system. As the infotainment systems in most vehicles provide the driver with information such as service schedules, tyre pressure and oil levels, there is a necessary connection between the infotainment system and the Controller Area Network (CAN) within the main vehicle network that connects all the ECUs together. It is therefore possible in many vehicles to pivot from the infotainment system to the CAN bus and inject commands, spoofing signals that would appear to be coming from, for example, the braking system ECU or the steering system.
As security researchers found in the widely-discussed Jeep Cherokee research2, a Renesas V850ES/FJ3 chip sits between the CAN bus and the head unit. It is configured to be read-only, receiving vehicle data from the CAN in order to inform the driver of current maintenance status, diagnostics and faults. The researchers studied and reverse engineered the V850 firmware, re-configured it to allow read/write permissions, to learn the CAN message sets and then successfully performed a firmware update. Like with most vulnerabilities, it took a few security researchers several weeks’ worth of effort to develop this capability, but once discovered, it could be weaponised and packaged into penetration testing tools.
There is of course variation in implementation and configuration between vehicle manufacturers, but there are three common weaknesses to all designs that are relevant to this attack objective. These are:
There are several ways an attacker could successfully disable the vehicle. One option would be to exploit smart device/convenience applications that tend to provide functions such as turning on lights, opening and closing windows and turning on Air Conditioning, each of which would allow an attacker to drain the car’s battery. Vulnerabilities have been found in a number of these applications, particularly with the authentication process. For example, Nissan launched a convenience app allowing access to the vehicle to access data such as current charge level and range, as well as to enable climate control in advance of the journey and other features. When pairing the smart device to the vehicle, the only authentication details required was the Vehicle Identification Number (VIN). The VIN is generally located at the bottom corner of the windshield, visible from the exterior21.
Track or monitor the vehicle
The modern vehicle holds and has an increasing potential to hold a great deal of personal data. Already, location, destinations/journeys, travel times, driving style/behaviour, contacts, messages, music preferences and even web-browsing activity is often captured. Increasing use of cameras for monitoring inside and outside the vehicle, as well as microphones for voice control and hands-free, creates opportunities for attackers to spy on the occupants to extract rich pattern-of-life data.
Use the vehicle as a weapon
The most sinister attackers may look to remotely control a vehicle to drive into a crowd of people, in a similar fashion to terrorist attacks already seen in Nice, Berlin, and other cities28. Autonomous Vehicles could potentially enable this style of attack to be executed remotely and at scale.
Malware
In addition to a ransomware attack described above, other forms of malware could be used to create botnets for cryptojacking or for launching Distributed Denial-of-Service (DDoS) attacks, leveraging the vast amount of computing power held within the 100+ ECUs. At its peak in September 2016, the IoT botnet ‘Mirai’ temporarily crippled several high-profile services such as OVH (one of the largest web hosting providers in the world) and Dyn (a popular DNS provider) via a large scale DDoS attack. OVH reported that these attacks exceeded 1 Tbps—the largest on public record. The Dyn attack took down a number of high profile web services including AirBnB, Amazon, Github, HBO, Netflix, Paypal, Reddit, and Twitter. These attacks were carried out via small, innocuous Internet-of-Things (IoT) devices like home
What are the top security risks for connected cars?
- Persona data theft
- Vehicle theft
- Connection risks
- Manipulation safety critical systems
- Mobile application security vulnerabilities
- Lack of designed in security
- Failure to keep up the security patch update
- IVI vulnerabilities
Author:

M A Ajay Velappan
Lead Engineer
Mahindra and Mahindra
He is Enthusiastic Electronics Engineer with a career span of 9 years on automotive industry. Rich experience in the areas of Connected Car, IoT, Infotainment. He has experience of working with global TIER-1s and global OEM. His hobbies are to go for plantation over weekend with NGO, and a vivid cricket enthusiast.