Security Considerations for Telematics Systems

Vehicle Telematics & Surface Attacks
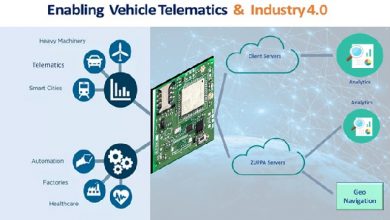
Telematics systems provide value-added features like remote diagnostics, crash response, and stolen car recovery over a long-range wireless link. These telematic systems connect in-vehicle networks with external communication centres via remote endpoints connectors.
The he introduction of the vehicle to vehicle and vehicle to infrastructure communication within the autonomous cars will broaden the possible attack surface. In recent years, the amount of attacks on in-vehicle networks has been began to grow dynamically.
The in-vehicle network may be a system for transferring data among different electronic control units (ECUs) of the vehicle via a serial data bus. As of today vehicles contain more than 70 ECUs, effective communication processes are required among them to succeed in their full functionality. The modern vehicle consists of over 100M lines of code, operating these ECU’s that manipulate all functionalities and everything from brakes, wipers, braking, and steering etc.
These ECUs interact in simple networks called controller area networks (CANs) that allow them to speak at high speeds. As vehicles adopt more and more technological applications and implemented connectivity functions to the external world, threats on electronic functionalities are rising exponentially.
With the arrival of the smartphone revolution and increased miniaturization, there has been a development of devices that attach to the on-board diagnostic (OBD-II) port that’s present in all modern cars. This port has traditionally been employed by engineers to download diagnostic data and run tests, but there’s a market emerging to permit car owners to access an equivalent data via their mobile device or maybe over the web . These OBD-II ports provide access to the CAN bus, potentially allowing direct manipulation of CAN traffic within the vehicle.
Various automotive serial protocols are used inside vehicles like Controller Area Network (CAN), Local Interconnect Network (LIN) and FlexRay. CAN bus is that the most used in-vehicle network protocol to support exchange of auto parameters between Electronic Control Units (ECUs). This protocol lacks security mechanisms and is therefore susceptible to various attacks. Furthermore, connectivity of vehicles has made the CAN bus not only vulnerable from within the vehicle but also from outside.
In-vehicle network security are often suffer from the degree of access protection considering the three aspects; remote endpoints, segmented network domains, and the location of critical ECUs. Any unprotected access points without a properly designed and installed gateway may leave a significant security gap for hackers to attack the in-vehicle network and thus threaten passenger safety.
The telematics system generates a huge amount of knowledge , it’s important to know how the info is handled and guarded . Expansive and multi-tiered, these systems are a mixture of physical hardware and software which will be complemented by an ever-expanding list of third-party integration options like Bluetooth beacons, temperature, tire pressure sensors, collision avoidance systems and in-vehicle cameras.
With numerous components involved, protecting telematics data requires a comprehensive, proactive approach dedicated to following best practices and also ensuring security at every stage.
(Image Source: DEKRA Digital GmbH)
Security Considerations
Safety–critical attacks against today’s vehicles require two general stages. the primary stage includes the injection of malicious data from outside using either remote or onboard access endpoints. The second stage requires to realize control over some ECUs or hack their functionality.
The degree of vulnerability is strongly influenced by the function of the hacked ECUs. Logical and physical segmentation methods should be applied to isolate controllers, safety–critical modules and network domains from external connection points to stop unauthorized access.
The way to build security confidence and safely exposing a telematics system to threats is by performing penetration tests, which are sanctioned hacking attempts performed either in house or by a corporation specializing in computer security.
During a penetration test, attempts are made to seek out vulnerabilities in hardware and software to seem into complete aspects:
- Implement secure data transfer
- Digitally sign updates
- Enable hardware code protection
- Assume your code is public so you are doing not believe secrets
- Use cryptographically strong hashing algorithms that can’t be reverse engineered
- Individualize security critical data
- Use different keys for various roles
- Monitor metadata to detect hacks
- Perform third-party auditing
- Limit server access
- Apply secure design practices
- Implement support for software/firmware updates
- Verify and test
Conclusion
Technology within vehicles will still evolve. From the controller area network, to the telematics gateway, to the backend services, and to the users themselves, security measures need to be implemented at every layer of the technology stack in order that the danger to driver safety and data is minimized.
The current infrastructure at both the cloud level and therefore the internal vehicle network has been demonstrably broken by researchers, and if active effort isn’t taken by automakers and telematics services providers alike to make sure a holistically secure ecosystem, more devious breaks of those systems could create massive problems for consumers within the future.
Author:
Ravindra Barlingay
Global R&D, Engineering & Technology Leader. Ex. Vice President R&D – Electronics, Advanced Engineering & eMobility at Endurance Technologies, Ex. Global R&D Leader for Embedded Systems, Connected Products, Systems & IoT at Schneider Electric and Ex. Group Head for Embedded Design & Development Centre at L&T Electrical & Automation
Published in Telematics Wire


One Comment